Previous episode
In the previous episode of the series instruction, we consider making manually a normal data profile with Wireshark for our software. That should protect our system from illegitimate data and create a secure environment. Manual data collection for a big company may be a long and boring task, however, quite flexible and comfortable for small and medium businesses. In that instruction, we will consider automation in making network data profiles that can help in different complicated and ambiguous situations. Let’s have a look!
Software
The first question appears: “What kind of software needs to use in this situation”? There are various types of programs, but we chose the logwatch and acct. They help to build automatic reporting and make profile systems which transform routine for easy movement.
Install and exploit
At the beginning write this command to update the index of the package :
sudo apt update –y && sudo apt upgrade –y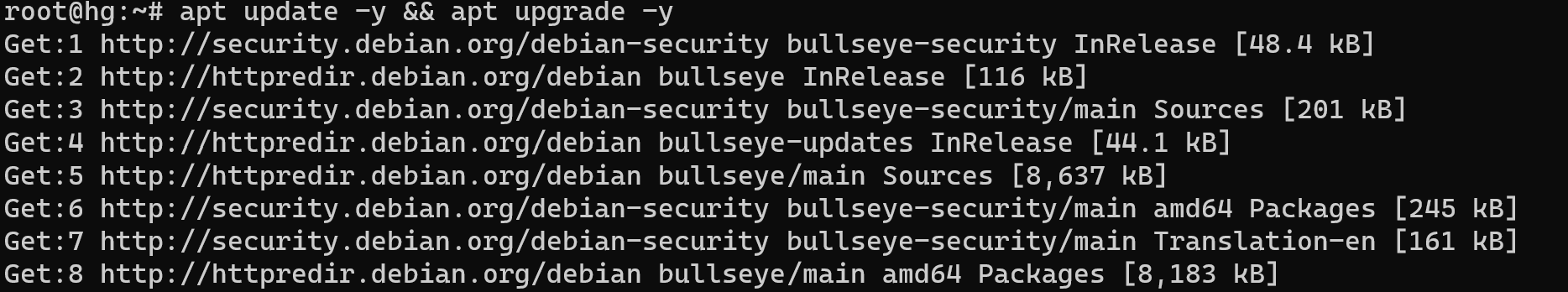
Wait a little bit of time to upgrade all packages this is a significant part of any installation. Right after this action write to CLI commands below, that install the needed software to our system:
sudo apt install acct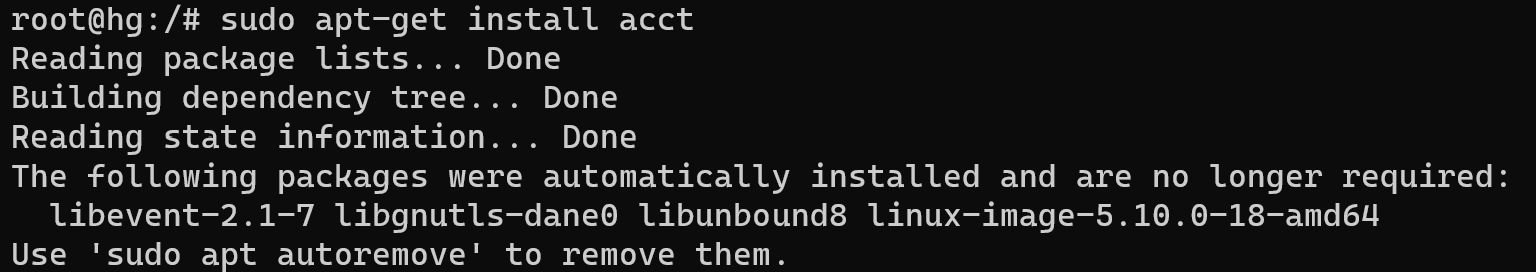
After this install system log–watching:
sudo apt install logwatch 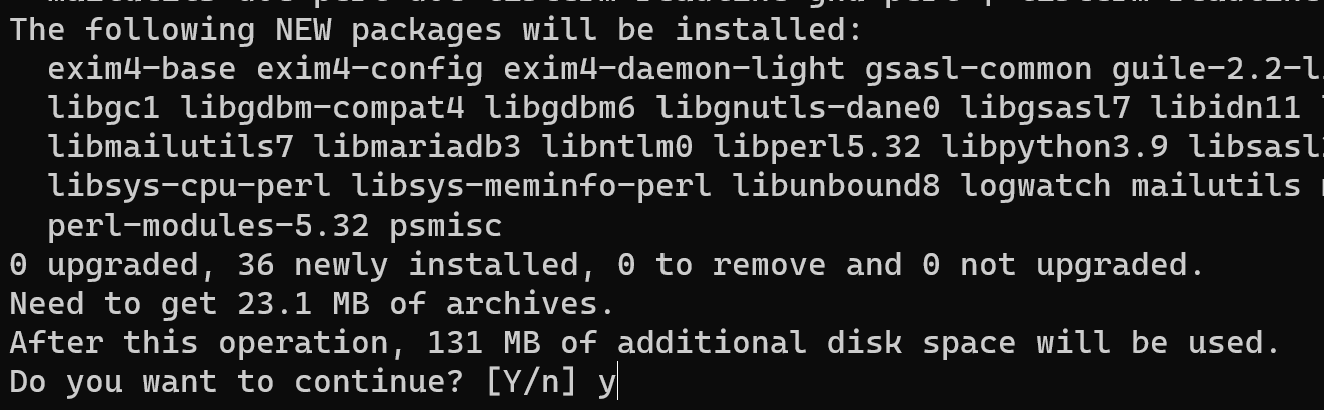
After installation look at the configuration file:
cd ~/usr/share/logwatch/default.conf && nano logwatch.conf 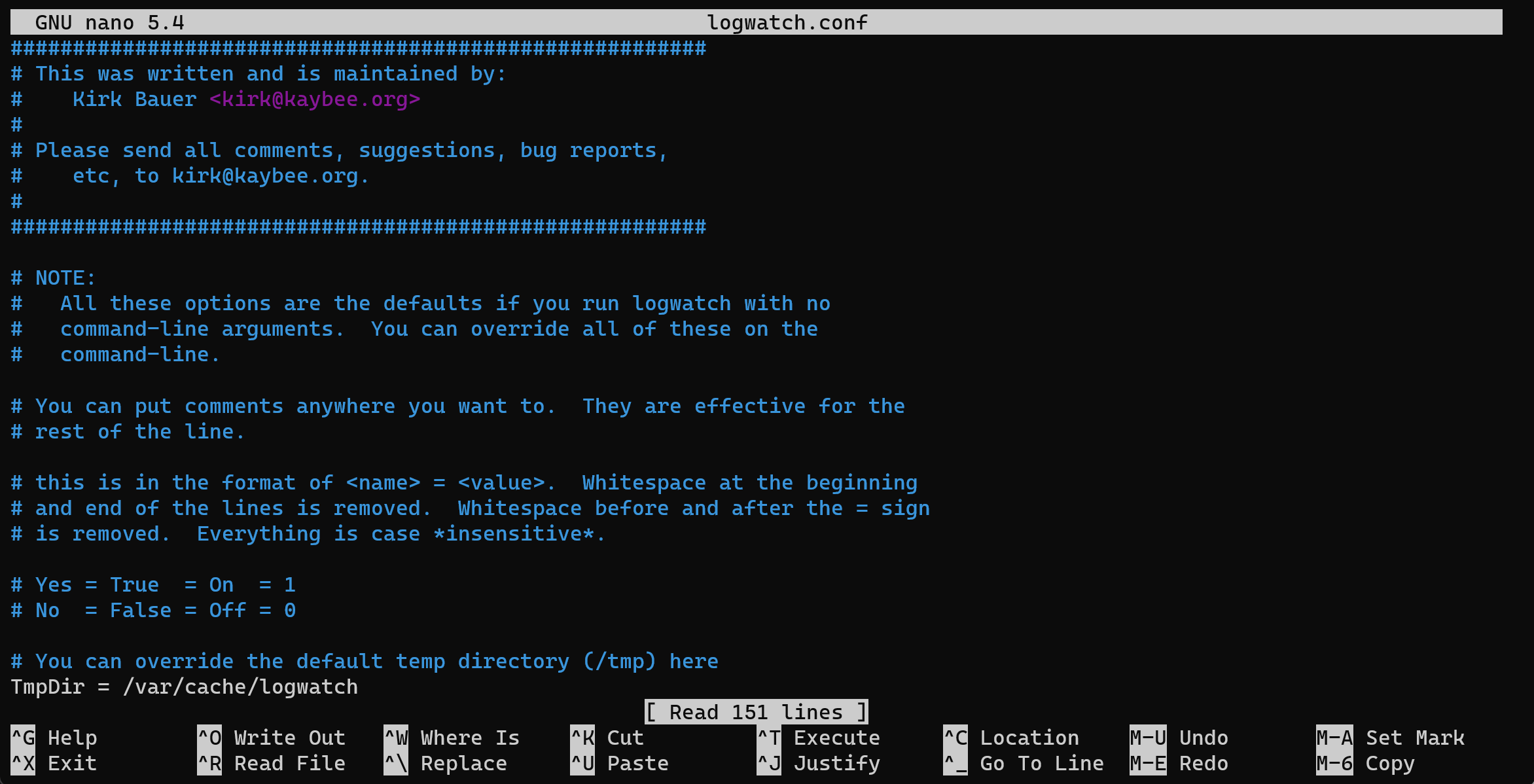
In this file, you can specify which logs should be analyzed, what level of detail of reports is needed, etc. If you want to gather log information about authentification then you need uncommented line:
LogFile = /var/log/auth.log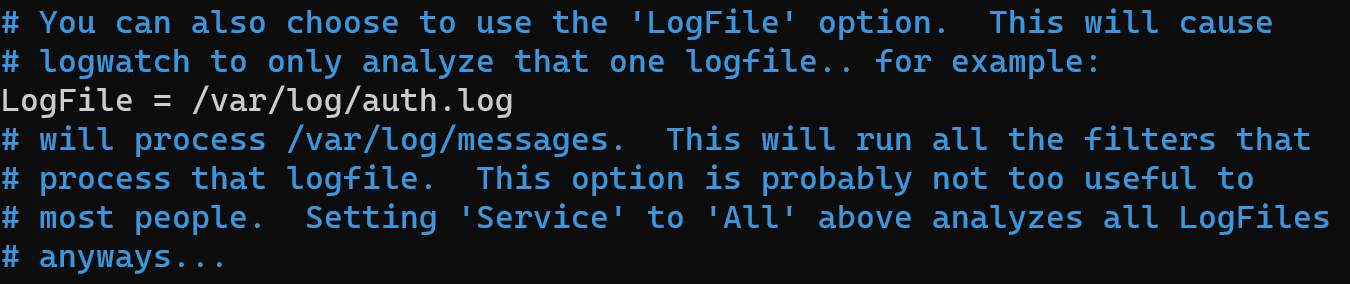
After compilating this setting if you have configured the SMTP server you can write in the config file data:
MailTo = an1ik@google.io
Then save the file with a combination of keys Ctrl+O, Ctrl+X and boot logwatch:
sudo logwatchAnd have a look at the results:
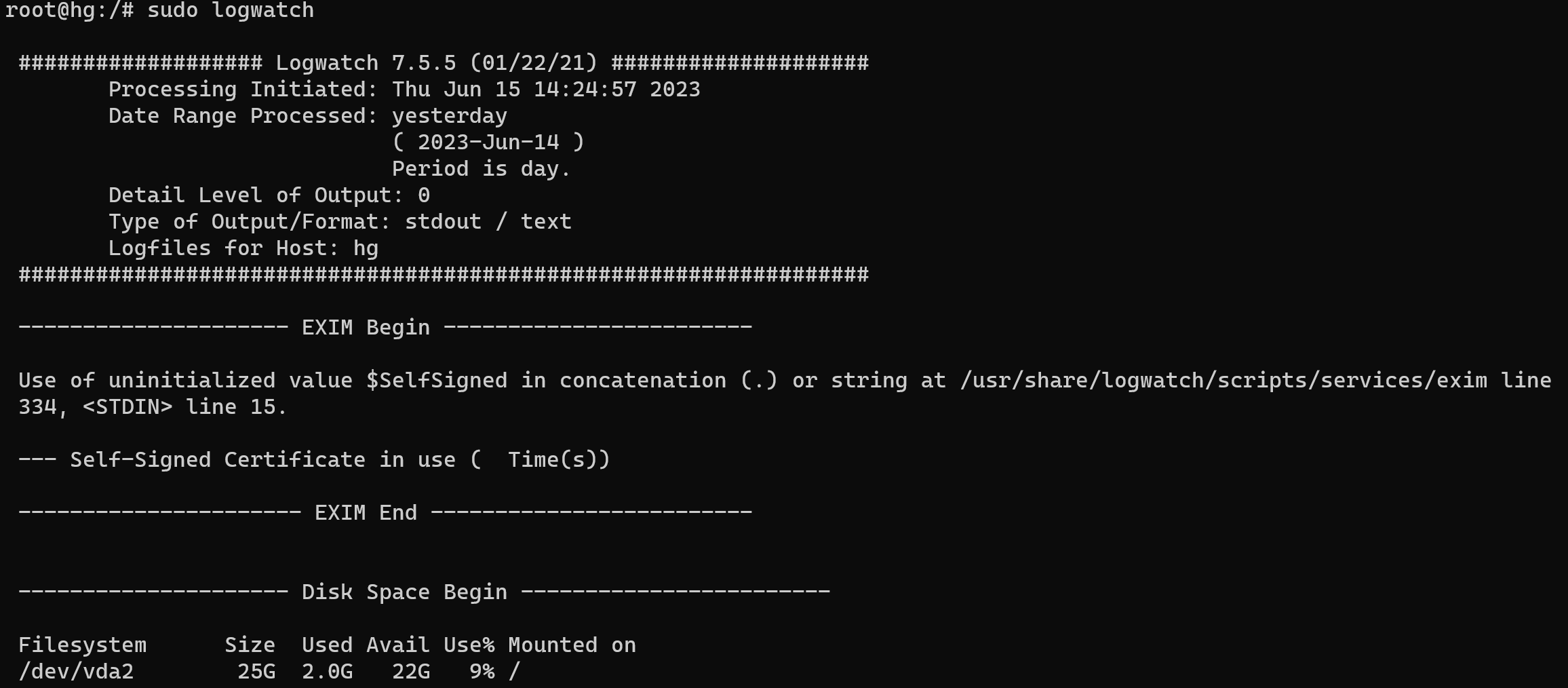
Now we go to use acct. After installing acct, you can enable its operation using the command:
sudo service acct start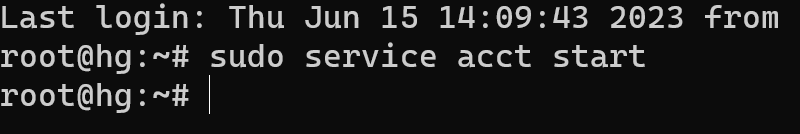
After this utility starts logging user information to /var/log/account/pacct. To view resource usage statistics for a specific user, you can use the sa command. For example, to view statistics for the user root, you need to run the following command:
ac –p /var/log/account/pacct root 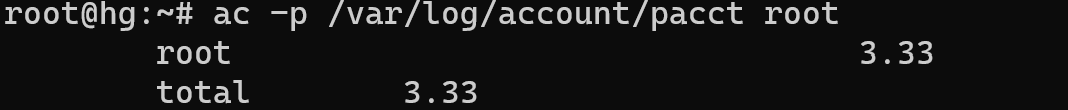
Conclusion
In that instruction, we installed monitoring and gathering system data utilities, which can automize collect and systemize information about logs from all systems and actions of users. It’s an additional digit print which we can use for our security system. In the next episode, we can touch on the creation of synthetic traffic and user profiles in the IPS/IDS system for protection. Don’t tune the channel!



