Introduction & Goals
In information security, there are three main aspects of any information: integrity, availability and confidentiality, which can be violated. The main problem in this situation is “threats”. Threats — it's a set of factors and processes which can cause damage to the information system and affect business task flow. One of the threats aimed at the availability of information — is DDoS.
Why do we care about this?
The attack intended to make a critical situation for us: unavailable servers due to overload systems. It can be forwarded to 3 layers: load hardware with volumetric requests, service and different apps can be violated by the attack because network transmission losses data and cluster, cloud same can be damaged.
And what to do about it?
Divide our infrastructure into two categories: internal and proxy layers. They will be responsible for the protection—formation of our infrastructure. At every stage, I will describe utilities and methods that represent complex and point ways of protection systems.
Protection Plan
Theory: Initially, I plan to implement a comprehensive approach to establish the primary layer of the defence system against potential DDoS attacks. Subsequently, I intend to employ targeted solutions to address any vulnerable areas that may have been overlooked by the initial safeguarding measures.
Practice: A rather complicated, but effective solution — “Traffic injection” that includes IPS/IDS, software for making false traffic, firewall, filters, load balancing, auto—scaling and virtual infrastructure. It’s already a set of point solutions united in a whole and interconnected system. That fits various types of architecture of networks.
Software & Installation
The first stage of the plan includes installing and deploying service gathering information and traffic analysis to make a profile of normal traffic.
Here are the generally recommended minimum system requirements:
- Processor: 2.5 GHz or faster;
- RAM: 2 GB (4 GB or more recommended);
- Hard disk space: 20 GB of available space;
- Operating system: Linux or Unix—based systems.
If your system parameters are alright, we can start the installation with the commands below:
sudo apt update && sudo apt upgrade -y
This command updates the index of packages and downloads required components. Install the necessary packages that include tools for traffic monitoring, log analysis, and others:
sudo apt install tcpdump -y
However, you can use another software due to system possibilities:
sudo apt install wireshark -yThis command downloads the necessary package for monitoring and sniffing traffic:
sudo apt install logwatch -y
It is necessary to establish control over the event log for making profiles:
sudo apt install acct -yTo collect information about users, you can use “acct”, but if you want, choose any available software for this purpose:
Configure parameters for gathering information according to the requirements of your information system. After analysis of network architecture, and your request for a protection—system — define the incoming and outgoing traffic flows for recording: Identify the user interfaces, port and IP address pul:
sudo tcpdump -i enp0s5 -s 0 -w output.pcap port 80
In this example the interface “ enp0s5” is used, the source defines like any IP address, port “80” and output file named “output.pcap”. Therefore I sniff traffic from the eth0 on port 80, HTTP traffic.
For Wireshark plane of usage will be the same:
sudo wireshark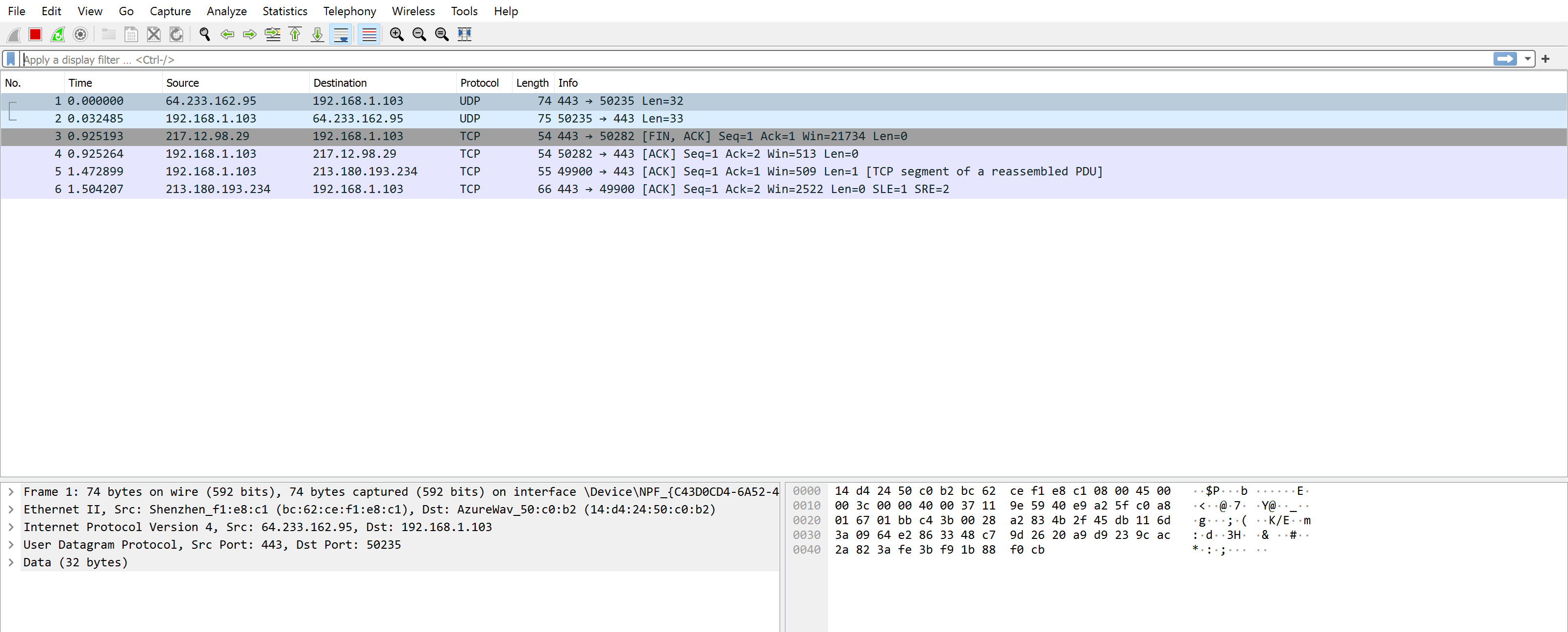
Choose the interface, click the button “Start” to begin sniffing traffic and “Stop” to finish, and then need to save the data dump. Click on” File” —> “Save” and choose the location and format for the saved file. Due to not small size of the dump data, recommend cleaning your system:
sudo apt-get autoremove && sudo apt-get cleanFor more detailed and accurate results start monitoring the system for 7 days. The more the better! Thus I collect data from the system and will make a profile of normal traffic. That process will be described in the next episode of instructions!
Conclusion
Setting up a gathering and sniffing system for DDoS attacks is a crucial step in protecting your network from malicious traffic. By using tools such as Wireshark and tcpdump, you can easily capture and analyze network traffic in real—time, helping to identify patterns and potential threats before they cause significant damage. It is essential to ensure that your system is properly configured and secured, as improper setup could lead to additional vulnerabilities. With the right tools and proper implementation, you can significantly reduce the risk of DDoS attacks and safeguard your network against cyber threats.



