WireGuard is an application that allows you to establish a secure virtual private network (VPN), known for its simplicity and ease of use. It uses proven cryptographic protocols and algorithms to protect data. Originally designed for the Linux kernel, it can be deployed on Windows, macOS, BSD, iOS and Android.
This WireGuard vpn setup uses Ubuntu 20.04.
Installing WireGuard Server on Ubuntu Linux
Log in via SSH to the Linux server, after logging in, check if the machine is updated by running the following command:
sudo apt-get update && sudo apt-get upgradeNow install WireGuard by running the following command:
sudo apt-get install wireguard
Setting up IP Forwarding
For VPN to work we need to enable packet forwarding, only then we will be able to connect through Wireguard server, to do this we need to edit /etc/sysctl.conf file:
sudo nano /etc/sysctl.confremove the "#" for the following command:
net.ipv4.ip_forward=1After that, run the following command to apply the changes:
sysctl -pThe following message will be displayed:
Generation of Private and Public Keys
WireGuard works by encrypting the connection using a cryptographic key pair. The key pair is used by passing the public key to the other party, which can then encrypt its message so that it can only be decrypted with the corresponding private key. To secure two-way communication, each side must have its own private and public keys, since each pair provides only one-way communication.
Before generating the key pair, go to the
dwg sudo cd /etc/wireguardSet the permission for this directory:
umask 077To generate a key pair, type the following command:
wg genkey | tee private.key | wg pubkey > public.keySetting Up the Server Configuration
To start configuring the WireGuard server, go to the /etc/wireguard folder and create the file wg0.conf
sudo nano /etc/wireguard/wg0.confAdd the following directives to the configuration file:
[Interface]
PrivateKey = <contents-of-server-privatekey>
Address = 10.0.0.1/24
PostUp = iptables -A FORWARD -i wg0 -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i wg0 -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
ListenPort = 51820
[Peer]
PublicKey = <contents-of-client-publickey>
AllowedIPs = 10.0.0.2/32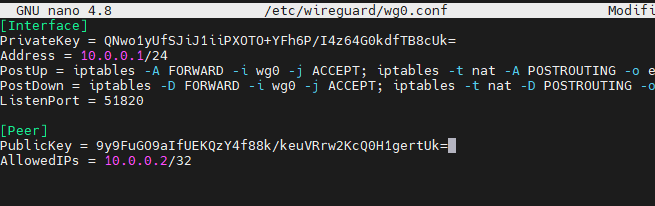
Copy the private key we generated earlier and paste it into the PrivateKey.
Similarly, we have to generate a key pair for the client, copy the client's public key and paste it into PublicKey.
To copy the key value, run the following command:
sudo cat /etc/wireguard/public.keysudo cat /etc/wireguard/private.keyLaunch WireGuard and Make It Start at Boot
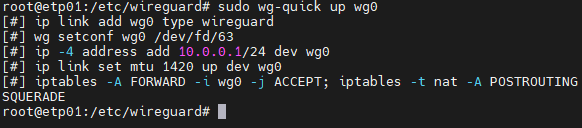
Now we are ready to start the server, to start WireGuard we use wg-quick and specify the name of the new interface:
wg-quick up wg0If the configuration is perfect, you will see the following screen,
To check the status of the WireGuard server enter:
wg show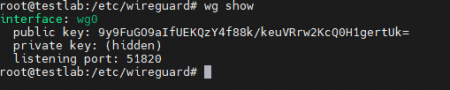
Congratulations, we have successfully started up the WireGuard server!




