How to Store and Manage BitLocker Recovery Keys in Active Directory (AD)
BitLocker is a built-in Windows feature that provides full disk encryption to protect data on workstations and servers. In enterprise environments, it is critical to securely store BitLocker recovery keys to ensure data can be recovered if users forget passwords or experience hardware issues.
In this guide, you will learn how to store and manage BitLocker recovery keys in Active Directory (AD). We’ll cover requirements, Group Policy configuration, key backup, and how administrators can retrieve recovery keys when needed.
Requirements
Before configuring BitLocker integration with Active Directory, ensure the following requirements are met:
- A computer with TPM version 1.2 or newer
- TPM enabled in BIOS/UEFI
- Secure Boot enabled (if supported)
- A Windows domain with Active Directory
- Administrative access to Group Policy Management
Creating a Group Policy for BitLocker Recovery Keys
To ensure BitLocker recovery keys are automatically stored in Active Directory, you must configure a Group Policy Object (GPO) that applies to domain computers.
First of all create object that you want to use in policy, for that open Windows Explorer by pressing combination of keys Win + E, next in the field above enter Control Panel\System and Security\Administrative Tools in that folder choose AD User and Computers:
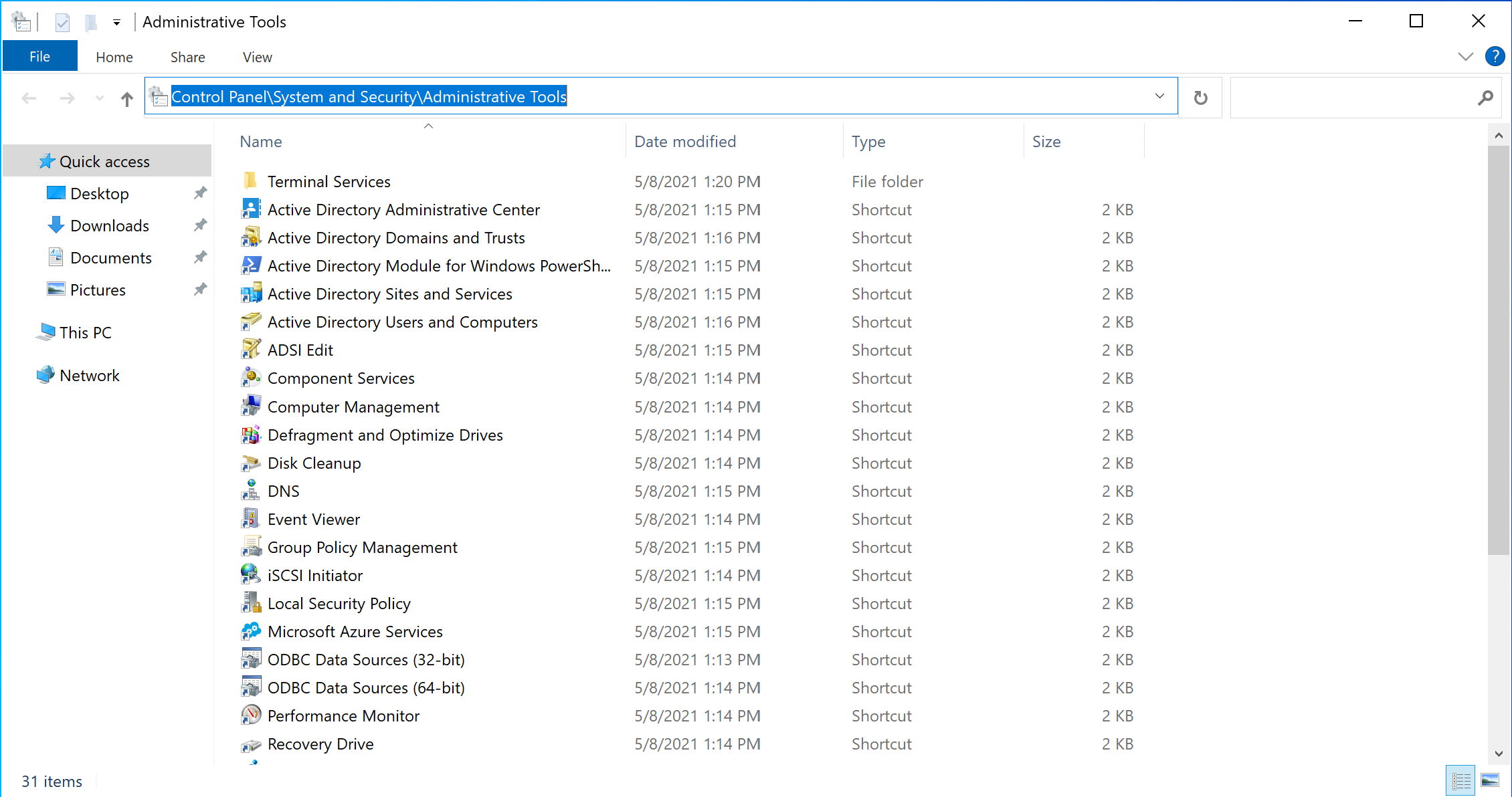
In that utility create new organization unit or object that you want to apply by policy of disk encryption, for that click on the domain name choose New and Organizational Unit:
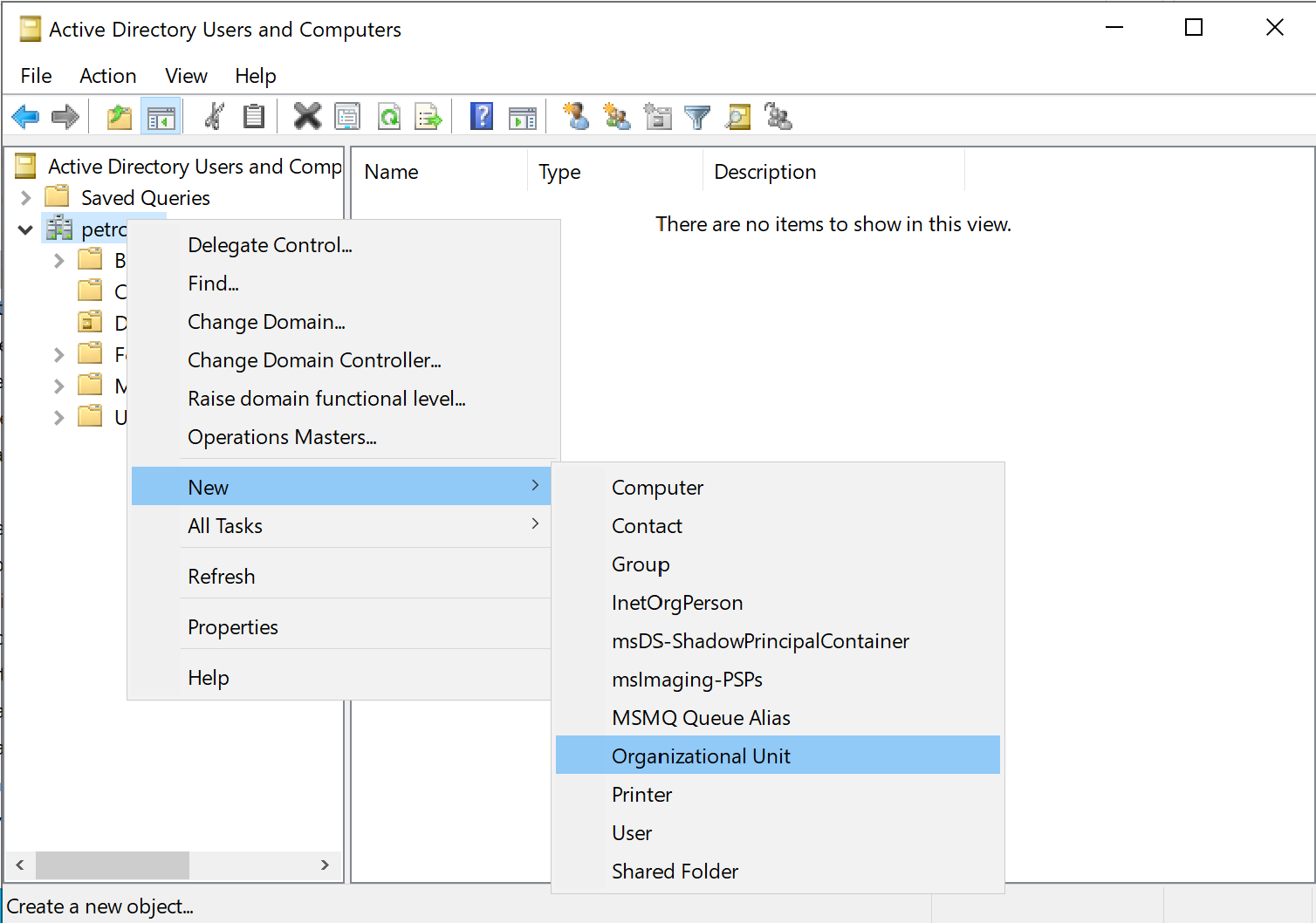
Add computer on your machine to OU:
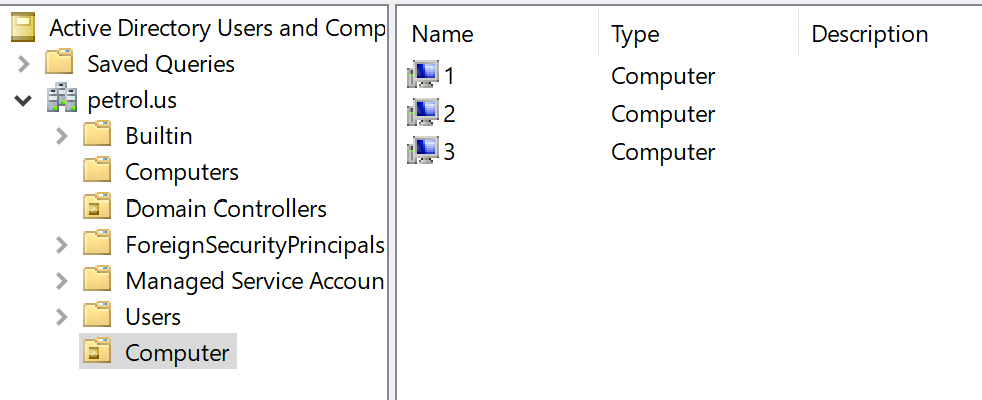
Locating the Group Policy management system is a breeze - simply conduct a search or utilize the following command by pressing Win+R:
gpmc.msc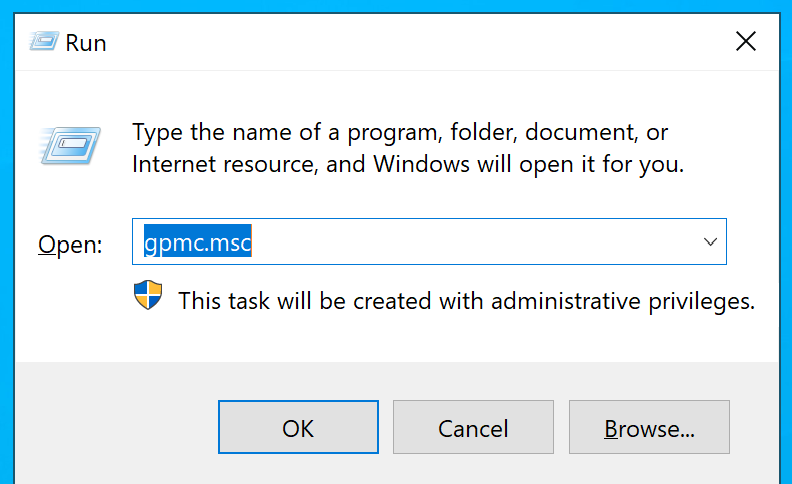
Next, establish a new group policy within the designated organizational unit that encompasses the computers where you desire to automatically store keys. For instance, you can apply it to the "Computer" OU. However, we can apply this for any objects in Active Directory: forest, domain, sites, OU or organizational unit all of that can be configured.
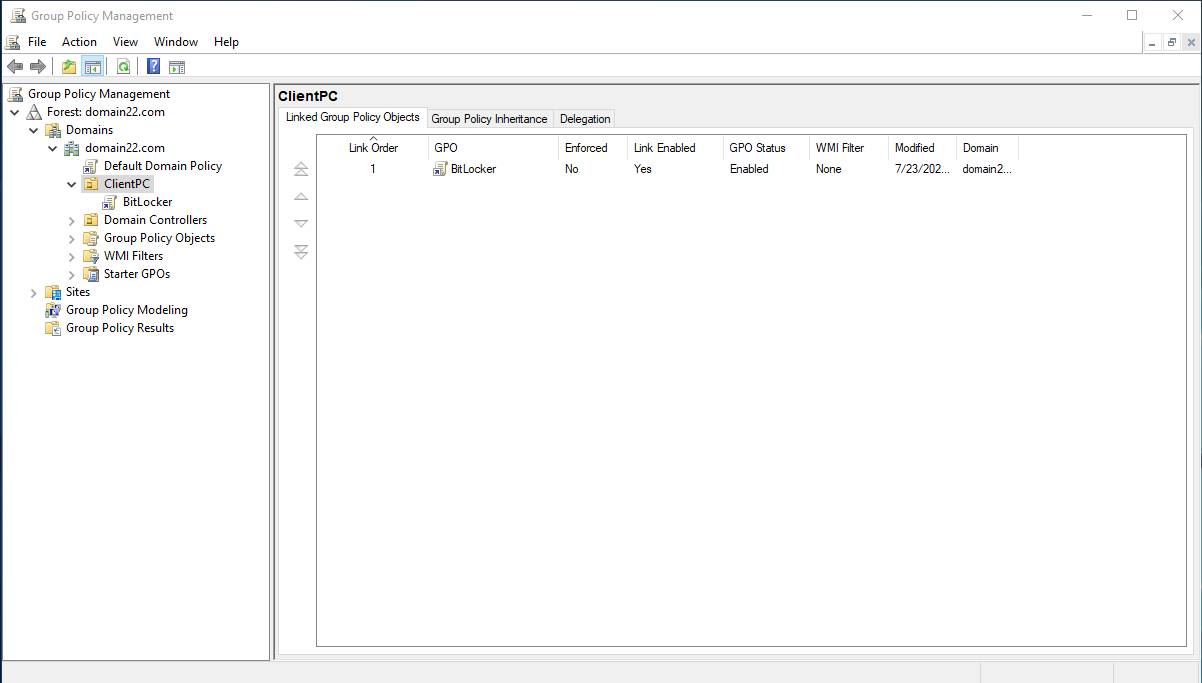
Click right mouse on the your object and choose accordance point as in the picture above:
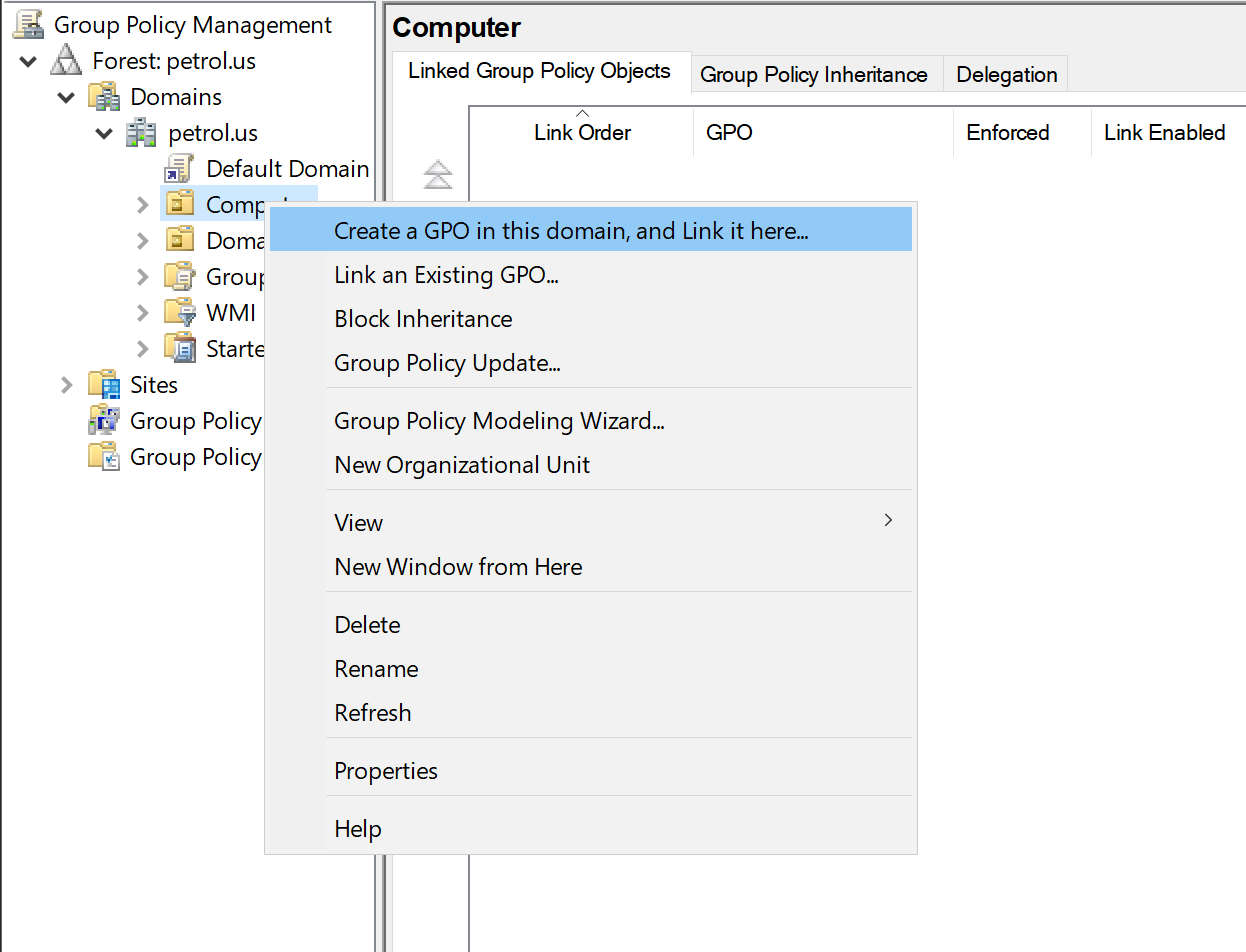
Setup GPO for domain
Begin by establishing a distinct Group Policy. Then navigate to the specified GPO section as illustrated below, and proceed to activate the Store BitLocker recovery information in AD policy option. Follow path Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> BitLocker Drive Encryption, choose that parameter and change value to Enabled.
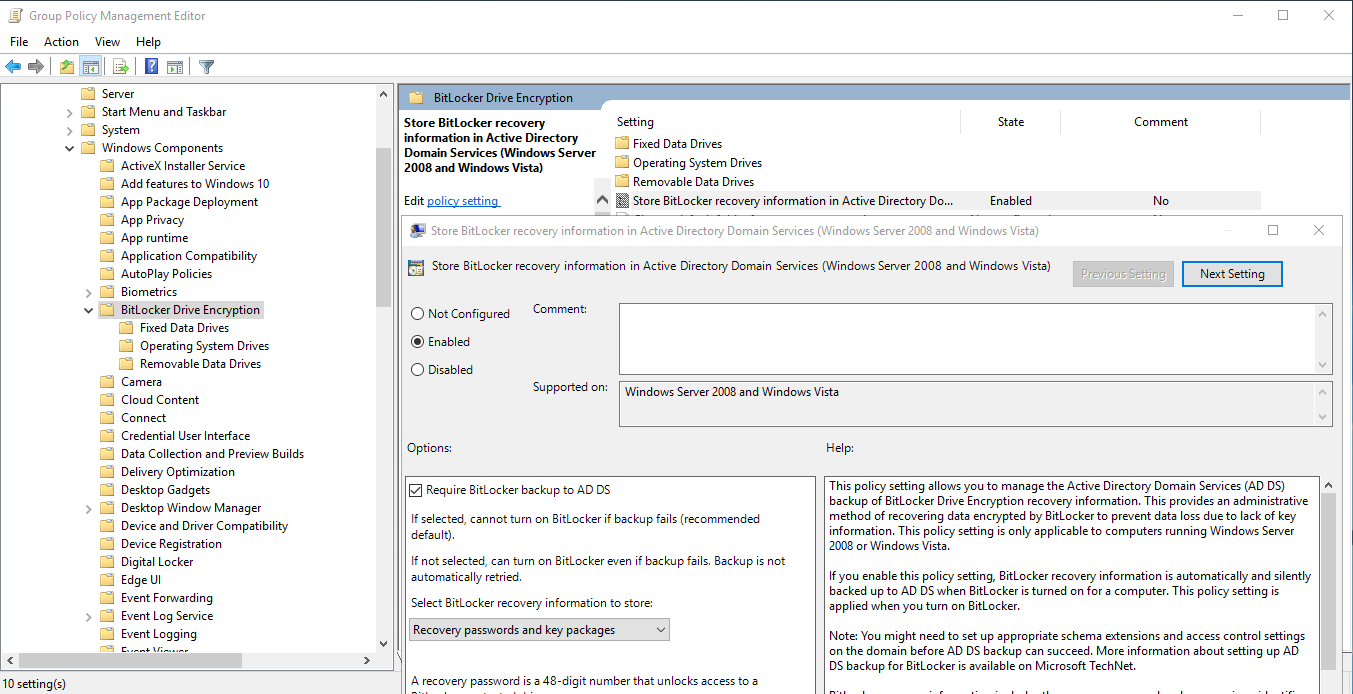
Let's continue the installation, now you need to go to the folder just below the menu list on the left and select the second Operating folder, which there will be a file with the Store settings, opening it with a double click, go to the panel and select Enabled.
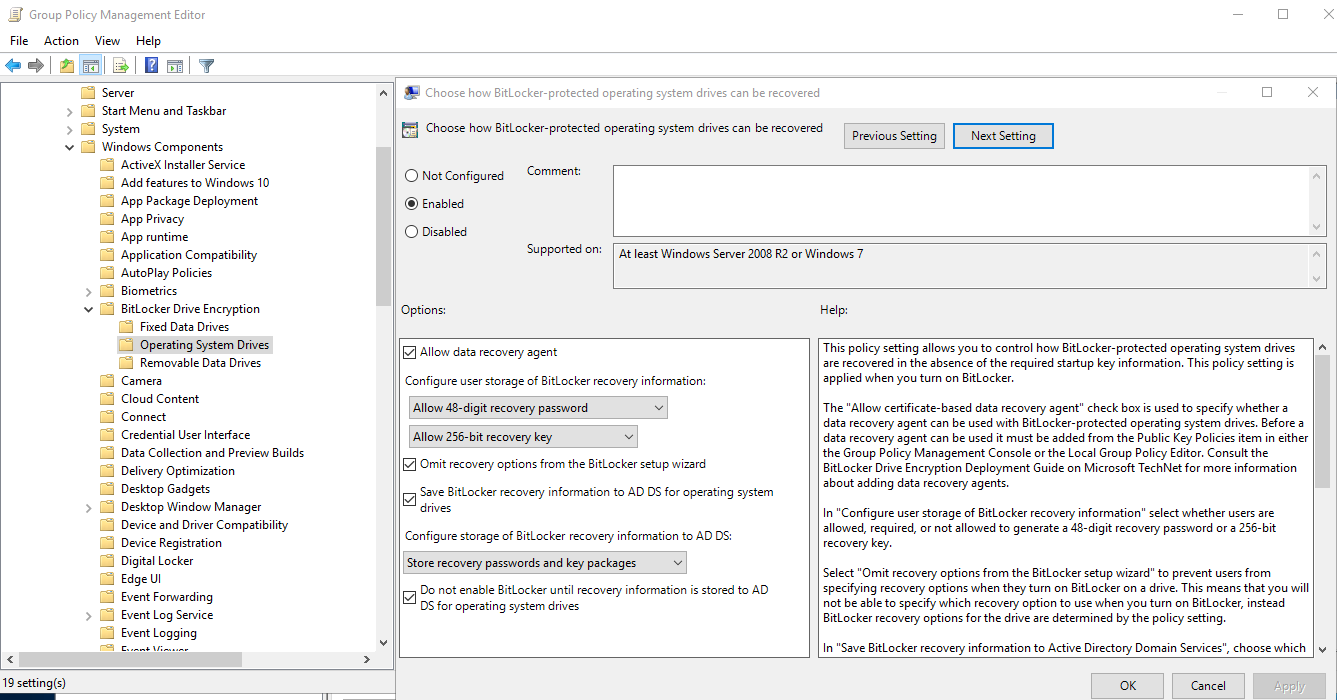
Check all box like in the screen above in options field then make sure that you chek last box due to potential issue of recovery. If you want save keys on removable device you need to choose accordance configuration file and Enabled that function.
Update policy
Next step will be update policy or rules that we configure in the step above, for that type command in the CLI and wait some time:
gpupdate /force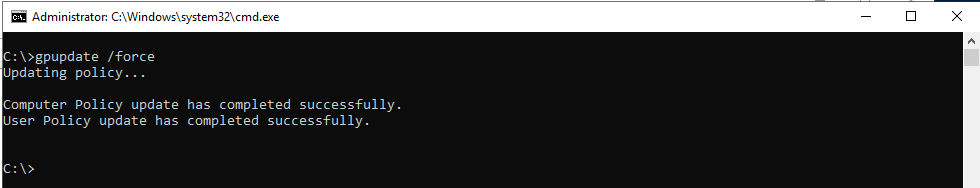
Managing BitLocker data in the AD
In order to effectively manage and configure BitLocker on client computers, it is imperative to install the required components on the server. By doing so, you gain the capability to oversee and fine-tune BitLocker settings, ensuring optimal security and encryption for the client machines:
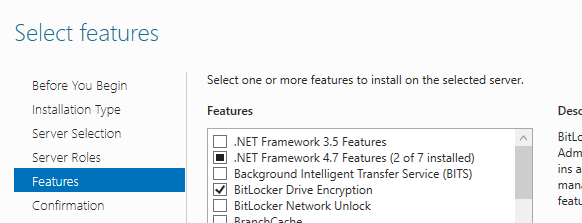
After successfully installing the component, a server restart is essential to complete the setup. Once the server is up and running, navigate to the Control Panel for AD users and components. Access the properties of the PC, where you will now find a new tab labeled "BitLocker Recovery." Within this tab, you gain the privilege to view the encryption key, providing essential insight into the BitLocker encryption status and recovery options for the PC.
In the event of a user encountering login difficulties, the domain administrator possesses the capability to retrieve the encryption key from the domain. Armed with this key, the user can effortlessly log in without any impediments. This seamless recovery process ensures swift access and minimizes potential disruptions caused by login complications, guaranteeing a smooth user experience.
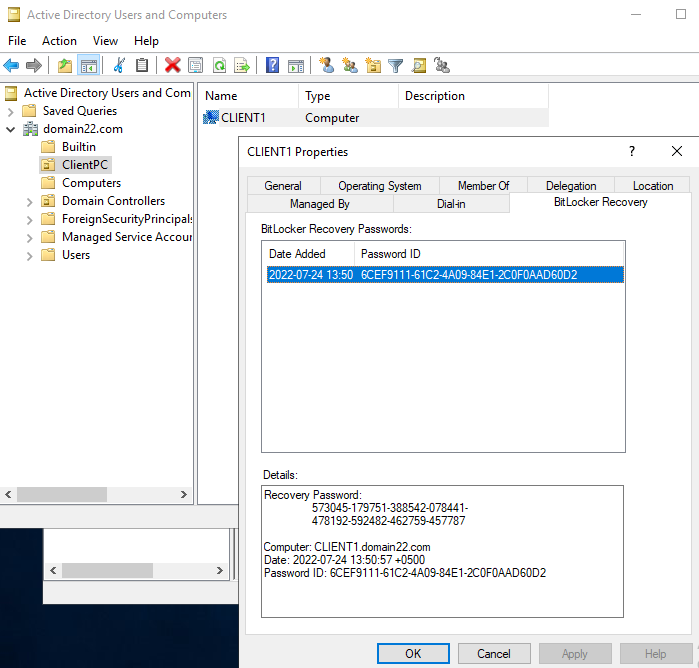
In case a user encounters login issues, the administrator holds the ability to retrieve the encryption key from the domain. With this key in hand, the user can effortlessly log in without facing any hindrance. This seamless recovery process ensures swift access and minimizes any potential disruptions caused by login complications.
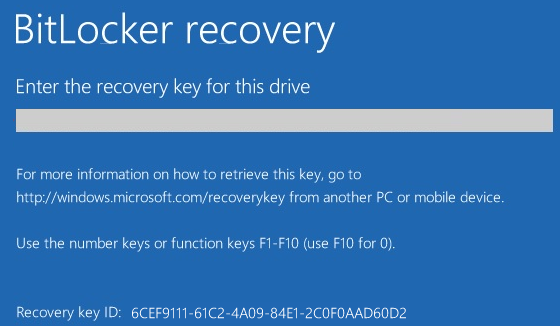
Recovery keys can be identified using the first 8 characters of the recovery password ID, making it easier to locate the correct key in Active Directory.
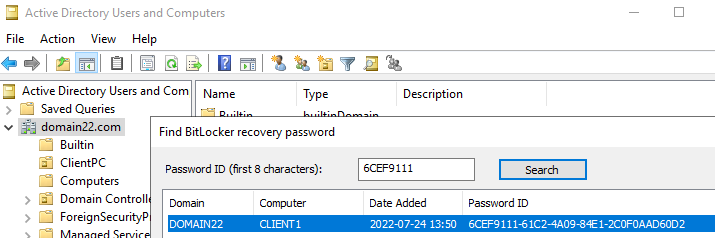
To ensure utmost security, exclusive access to the BitLocker key is granted solely to the domain administrator. Nevertheless, if needed, permissions can be adjusted to provide other domain users with access to the BitLocker key. This flexibility enables a controlled and well-managed approach to granting key retrieval rights, thus empowering the appropriate personnel to access and manage the BitLocker recovery process as required.
Enabling BitLocker Encryption on the Drive
Once the recovery key is backed up to Active Directory, BitLocker encryption can be safely enabled on the drive.
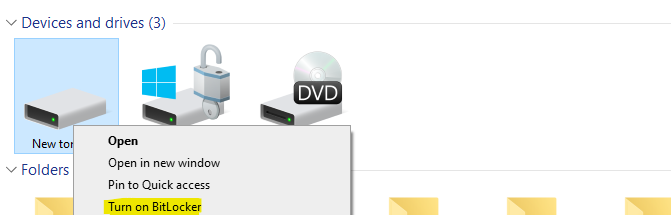
Once your key is securely stored in the domain, BitLocker automatically initiates the encryption process for the drive. This streamlined approach ensures seamless data protection.
Moreover, you have the flexibility to utilize multiple BitLocker passwords on a single PC, each associated with different portable flash drives. This versatile feature allows for convenient and tailored data encryption for various storage devices.
Is disk encrypted?
If you encrypted your disk before that step, then you need to know their ID and add them to the system storage for recovery purposes:
manage-bde -protectors -get c:By executing this command, you gain access to the comprehensive details of the BitLocker encryption protectors associated with the specified drive. Replace "c:" with the letter corresponding to the specific drive you wish to inquire about. Upon running the command in either Command Prompt or PowerShell, pertinent information like recovery passwords, recovery keys, or TPM protectors (depending on the encryption method employed for that drive) will be displayed.
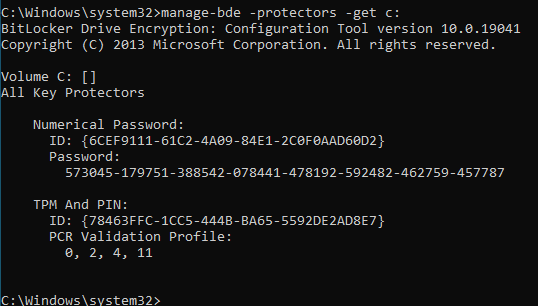
In that process we need to retrieve a ID (e.g., 6CEF9111-61C2-4A09-84E1-2C0F0AAD60D2).
To continue, follow the setup instructions and proceed to enter the next command in the provided interface. This pivotal step ensures the seamless progression of the configuration process, unlocking the full potential of BitLocker encryption.:
manage-bde -protectors -adbackup C: -id {6CEF9111-61C2-4A09-84E1-2C0F0AAD60D2}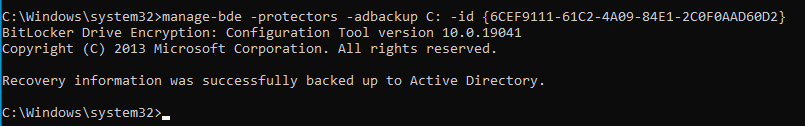
With this command, the specified key will be securely backed up in Active Directory, ensuring the enhanced protection and recovery of your encrypted drive.
Result
In this guide, we demonstrated how to store and manage BitLocker recovery keys in Active Directory using Group Policy. Centralized key storage ensures secure recovery, simplifies administration, and reduces the risk of permanent data loss.
Proper BitLocker and AD integration is a critical component of enterprise data protection strategies, helping organizations maintain security while ensuring operational continuity.
FAQ - BitLocker Recovery Keys in Active Directory (AD)
- Q: What is the purpose of storing BitLocker recovery keys in Active Directory?
A: Storing BitLocker recovery keys in AD centralizes key management, ensuring secure storage and easy retrieval if users encounter login issues or lost encryption keys. - Q: Who can access BitLocker recovery keys in AD?
A: By default, only domain administrators have access to the recovery keys. Permissions can be configured to grant specific users or groups access if necessary. - Q: How do I back up a BitLocker key to Active Directory?
A: Use the manage-bde -protectors -adbackup command with the key ID of the encrypted drive to securely store the recovery key in AD. - Q: What are the requirements for integrating BitLocker with AD?
A: You need a TPM-enabled computer (version 1.2 or higher), BIOS/UEFI with TPM enabled, Secure Boot (if supported), and appropriate Group Policy configuration in your domain. - Q: How can I check if a drive is encrypted with BitLocker?
A: Use the command manage-bde -protectors -get <drive letter>: in Command Prompt or PowerShell to view encryption status, recovery passwords, and TPM protectors. - Q: Can multiple BitLocker passwords be used on a single PC?
A: Yes, you can assign multiple recovery passwords to a single PC, including those associated with different removable drives, to provide flexible encryption management. - Q: Where are BitLocker recovery keys stored in Active Directory?
A: Recovery keys are stored as attributes of the computer object in Active Directory and can be viewed by authorized administrators.
 700
300
700
300
 700
300
700
300
 700
300
700
300


