Proper network configuration is the foundation of security, availability, and performance for any IT infrastructure. Whether you manage a small business server or deploy complex systems for large enterprises, a well-planned and secured network minimizes risks, enhances fault tolerance, and ensures stable operations. This article outlines a step-by-step network setup process: from infrastructure planning to firewall configuration. It targets system administrators, DevOps engineers, and technically skilled SMB owners. However, for production environments, engaging qualified specialists is strongly recommended.
Real-World Examples:
- Small Business:
- An e-commerce store processing online payments requires customer data protection (PCI DSS compliance) and uninterrupted operation during hardware failures.
- Enterprise:
- A distributed office network with branches across cities needs fault tolerance (backup communication channels) and DDoS protection.
- DevOps Team:
- Deploying a microservices architecture in the cloud demands network flexibility for container support (Kubernetes) and scaling.
Planning and Prerequisites
Infrastructure Design
The first step is selecting your network's core server type:
- Virtual Machine (VM):
- Ideal for local environments or testing
- Popular hypervisors:
- VMware ESXi: High performance, enterprise features
- Microsoft Hyper-V: Windows ecosystem integration
- KVM: Free, open-source
- Cloud (VPS/VDS):
- Optimal for scalability and remote access
- Providers:
- AWS EC2, Google Cloud, Azure
- Yandex Cloud: Local solutions for RU audiences
- VPS/VDS from hosts (DigitalOcean, Hetzner)
Load Assessment:
- Traffic:
- Website: Requests per second (RPS), data transfer size
- Streaming: Video bitrate (5 Mbps per user)
- Peak Loads:
- E-commerce during sales: 1,000+ concurrent users
- Corporate network: 50+ employees with VPN
Hardware Requirements
CPU:
- Minimum: 2 cores (Intel Core i3, AMD Ryzen 3)
- Recommended: 4+ cores (Intel Xeon E5 v4+, AMD EPYC Milan)
RAM:
- Minimum: 4 GB
- Recommended: 8+ GB (16+ GB for databases)
Storage:
- Minimum: 50 GB SSD
- Recommended: 100+ GB NVMe with RAID 1
NICs:
- Minimum: 1 Gbps
- Recommended: 2+ cards with LACP
Additional: Hardware routers (MikroTik, Cisco) or firewalls (Fortinet, pfSense)
OS Selection
Linux:
- Ubuntu Server 22.04 LTS: Easy setup
- Debian: Stability
- CentOS Stream/Rocky Linux: Enterprise environments
Windows Server 2022:
- For Active Directory, MS SQL
- Requires licensing
Recommendation: Linux (Ubuntu/Debian) for security and efficiency
Network Diagram
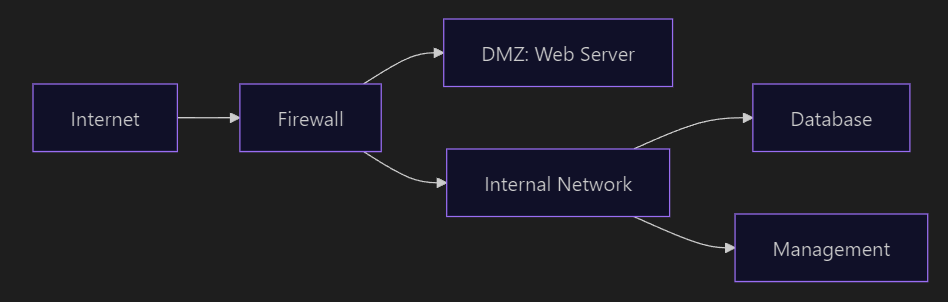
DMZ: Isolates public services
VLANs:
- VLAN 10: Management
- VLAN 20: Data
- VLAN 30: Guest Access
pfSense Example:
WAN (DHCP/Static) → LAN (192.168.1.0/24) → DMZ (192.168.2.0/24)
Rules: Allow HTTP/HTTPS only from WAN to DMZIP Addressing
- Public IPs: For external access
- Private IPs (RFC 1918):
- 192.168.0.0/24
- 10.0.0.0/8
- NAT:
sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
OS Installation and Basic Setup
General Steps:
- Download ISO image
- Create bootable USB (Rufus or
dd) - Minimal installation (no GUI)
- Configure language, timezone, user
🔒 SSH Security:
sudo sed -i 's/#PermitRootLogin yes/PermitRootLogin no/' /etc/ssh/sshd_config
sudo systemctl restart sshdChecklist:
- System update (
apt update && apt upgrade) - NTP synchronization
- Disable unused services
Basic Network Configuration
Assign Static IP
Ubuntu (/etc/netplan/01-netcfg.yaml):
network:
ethernets:
enp0s3:
addresses: [192.168.1.10/24]
gateway4: 192.168.1.1
nameservers:
addresses: [1.1.1.1, 1.0.0.1]
version: 2Apply: sudo netplan apply
CentOS/Rocky (/etc/sysconfig/network-scripts/ifcfg-enp0s3):
DEVICE=enp0s3
BOOTPROTO=none
ONBOOT=yes
IPADDR=192.168.1.10
NETMASK=255.255.255.0
GATEWAY=192.168.1.1
DNS1=1.1.1.1
DNS2=1.0.0.1VLAN Tagging
vlans:
vlan20:
id: 20
link: enp0s3
addresses: [192.168.20.2/24]LACP Aggregation
bonds:
bond0:
interfaces: [enp0s3, enp0s4]
parameters:
mode: 802.3adDNS Configuration
/etc/resolv.conf:
nameserver 1.1.1.1
nameserver 1.0.0.1Network Testing
ping 8.8.8.8 # Internet access
nslookup google.com # DNS functionality
iperf3 -c server_ip # Bandwidth test
traceroute 8.8.8.8 # Routing checkFirewall Configuration
Tool Selection
iptables: Powerful, complex</code>
<code>ufw: Simplified (Ubuntu)</code>
<code>firewalld: Flexible (CentOS/Rocky)
🔒 Core Rules
ufw (Ubuntu):
sudo ufw default deny incoming
sudo ufw default allow outgoing
sudo ufw allow from 192.168.1.0/24 to any port 22
sudo ufw allow 80/tcp
sudo ufw allow 443/tcp
sudo ufw enablefirewalld (CentOS/Rocky):
sudo firewall-cmd --set-default-zone=drop
sudo firewall-cmd --permanent --zone=trusted --add-source=192.168.1.0/24
sudo firewall-cmd --permanent --zone=trusted --add-service=ssh
sudo firewall-cmd --permanent --zone=public --add-service=http
sudo firewall-cmd --permanent --zone=public --add-service=https
sudo firewall-cmd --reloadVerification
sudo ufw status verbose # ufw
sudo firewall-cmd --list-all # firewalld
sudo tcpdump -i eth0 port 80 -vv # Traffic monitoringSecurity Checklist:
- Only essential ports open (22, 80, 443)
- SSH access restricted to trusted IPs
- Inbound connections denied by default
- Rule testing completed
Core elements of a secure network:
- 🔒 Security: Block unused ports, restrict SSH access
- ⚙️ Fault Tolerance: RAID arrays, LACP, backup channels
- 📊 Monitoring: Regular log and performance reviews
- 💾 Backups: Automated backups for critical data
Recommendations:
- Use centralized monitoring (Zabbix, Prometheus)
- Regularly update software and audit security
- Engage network engineers for complex infrastructures
⚠️ Critical! After firewall setup, verify service accessibility!



