Modern network infrastructure heavily relies on Linux, which provides a powerful mechanism for controlling system resources with precision. Linux offers a multi—user environment that permits multiple users to log in and work on the system simultaneously. However, not all users require equal access to system resources or possess the same level of trustworthiness.
To address these concerns, administrators can utilize various techniques to limit user permissions, ensuring that each user has access only to the resources necessary to complete their tasks. One such software option that can be used for this purpose is being considered in this instruction. In the previous episode, we consider the express profile building, if you didn't see that yet check it out!
Software
Restricting user rights involves configuring security parameters of different config files: users, groups of users or processes. This can be done using built—in system permission, user groups or tools like AppArmor. System permission gives access to specific information systems subjects.
Availabilities such as writing, reading and executing access to the object of the file system. AppArmor and other software can be security modules which provide security services via the MAC concept and confinement process subset of the system.
Install and exploit
Before using the main utility update and upgrade your system:
sudo apt update -y && sudo apt upgrade -y
The main components of secutiy module are already built into Debuan server. However, management resources and tools you need to download separately, absolutely the same things with profiles, it is install manually:
sudo apt install apparmor-utils apparmor-profiles -y
Let's make sure everything is working correctly and execute the following command:
sudo apparmor_status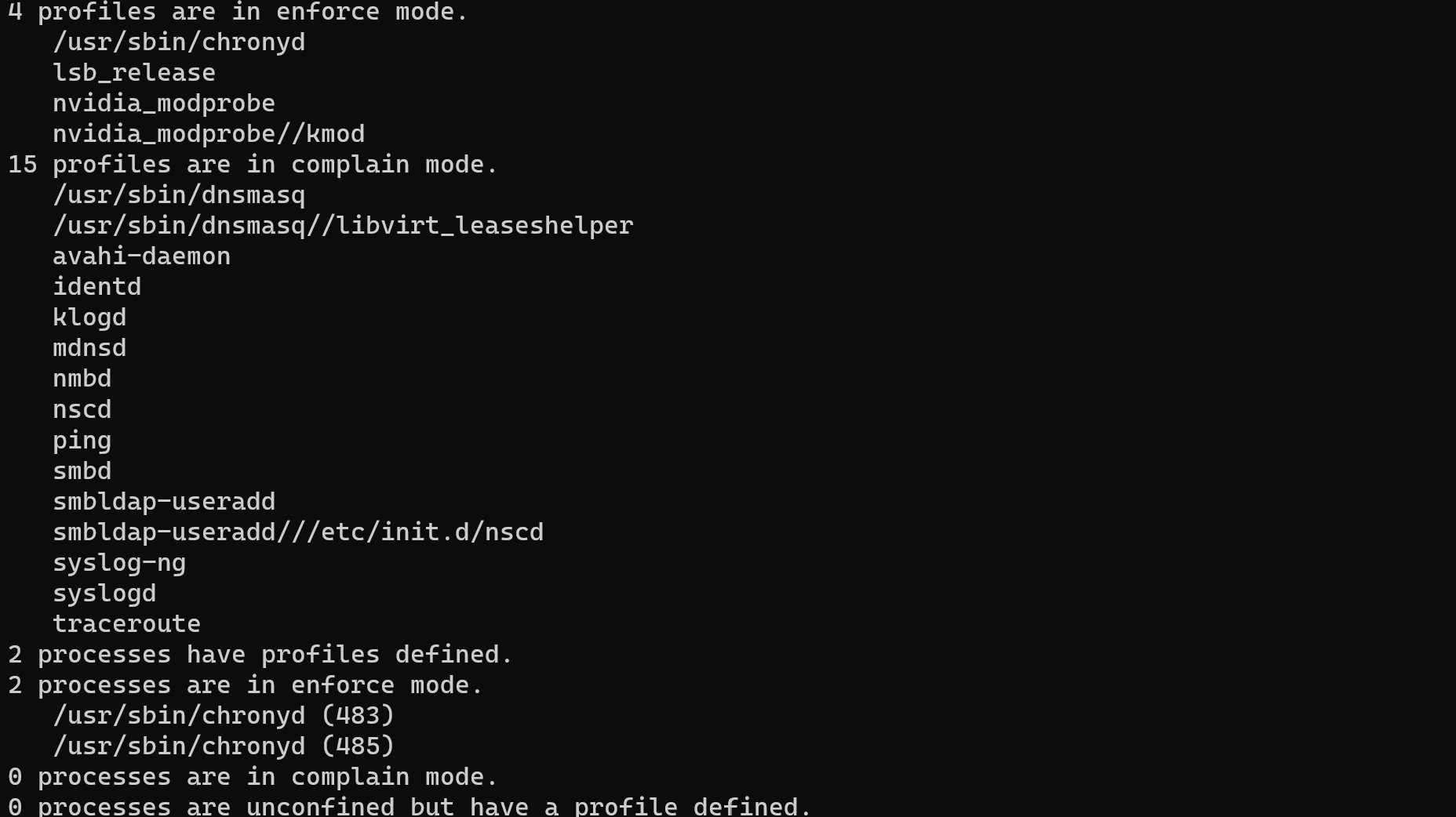
For deepest and more flexible configuration we can use created profile by community and developers, they help rapidly make a setup for determine tasks. So, to open this profiles write command:
sudo ls -l /usr/share/apparmor/extra-profiles/ |head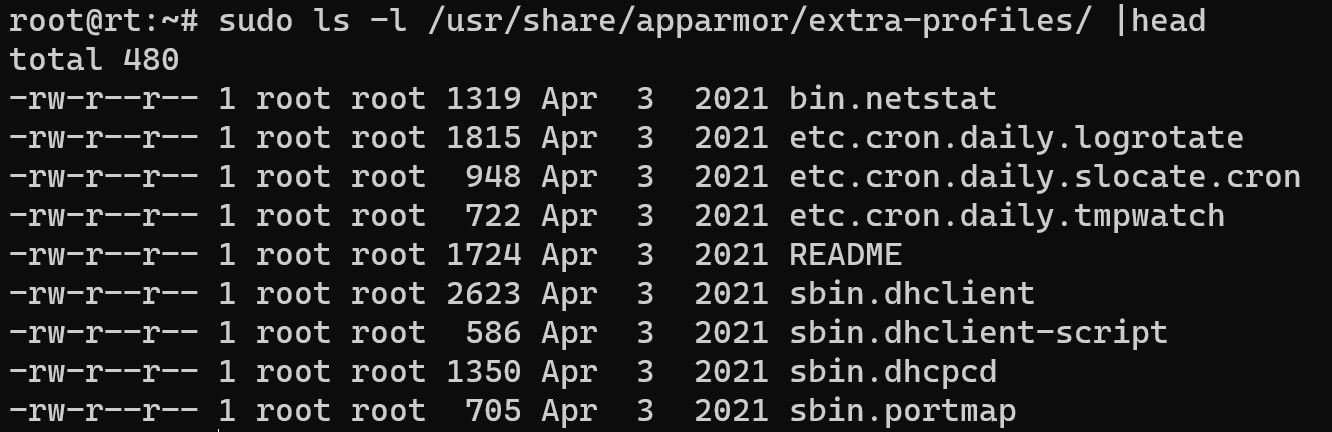
We can see more than 100 ready to use profiles and can setup them:
sudo cp -r /usr/share/apparmor/extra-profiles/ /etc/apparmor.d/
Command copy template for worker folder and activate them. For more detail configuration look at the profile, with command open them:
sudo apt install nano -y && nano /etc/apparmor.d/bin.ping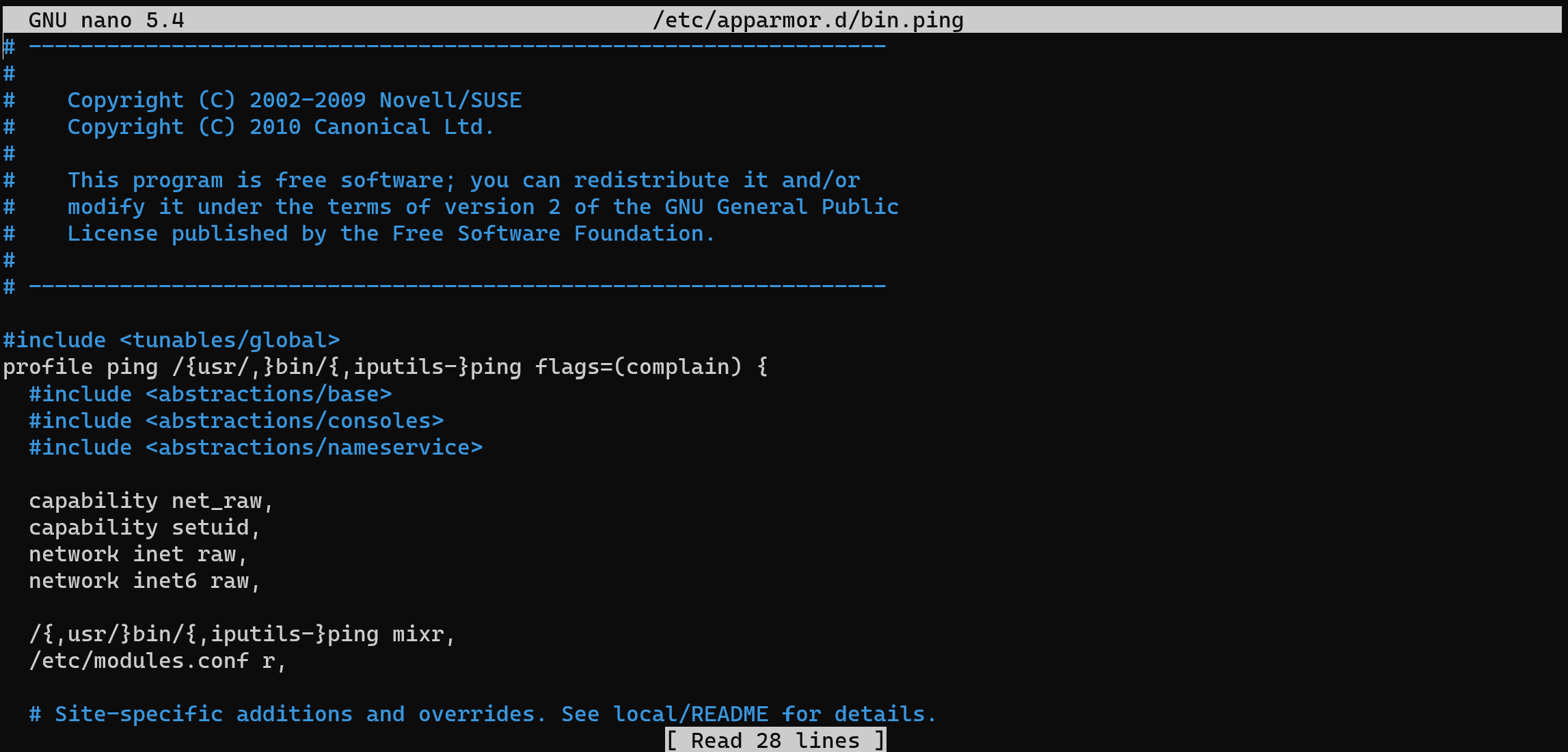
#include <tunables/global>
profile ping /{usr/,}bin/{,iputils-}ping flags=(complain) {
#include <abstractions/base>
#include <abstractions/consoles>
#include <abstractions/nameservice>
capability net_raw,
capability setuid, network inet raw,
network inet6 raw,
/{,usr/}bin/{,iputils-}ping mixr, /etc/modules.conf r,Press Ctrl + O for save and Ctrl + X for exit. Consider different file so they have a little bit simple configuration settings. Let’s have a look to a parameters:
- profile ping /{usr/,}bin/{,iputils—}ping flags=(complain): This declares a new AppArmor profile named ping that applies to the ping command, which is located at /bin/ping or /usr/bin/ping or /usr/bin/iputils—ping. The flags=(complain) option tells AppArmor to log violations of this profile instead of enforcing them immediately;
- #include <abstractions/base>: This includes the base abstractions for the system, which provides common access patterns and rules for file paths, capabilities, and other resources;
- #include <abstractions/consoles>: This includes rules for accessing console devices;
- #include <abstractions/nameservice>: This includes rules for accessing name service databases like DNS.
By changing these parameters, you can more accurately and flexibly configure the system to meet your specific task.
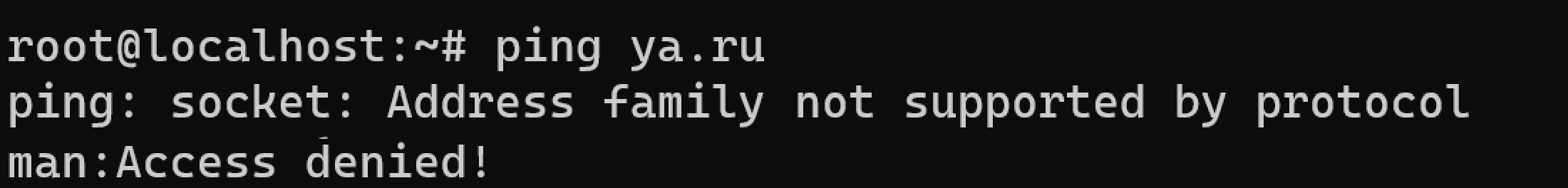
Check permission for ping template:
Conclusion
Restricting user permissions is an essential aspect of managing Linux systems. It allows administrators to ensure that users only have access to the necessary resources and reduces the risk of security breaches. AppArmor is a powerful tool that can help administrators restrict user permissions by defining specific profiles for users and their associated processes.
By following the steps outlined in this article, administrators can create AppArmor profiles and log files, analyze them, and enforce restrictions on user permissions. Ultimately, implementing these techniques will lead to a more secure and efficient Linux system.



