Introduction
Small and medium businesses have many problems with network architecture: old server hardware, lack of IT — employees, whole mechanism open to attackers! There are local but vital solutions that can help in this crucial situation. Proxy — server is such a detail of a giant mechanism of protection. It has a set of explicit opportunities: redistributions data-load on a server, IPS and IDS and creating simplicity anonymity, by replacing IP-address in a data header. One of these solutions is presented as HAProxy.
The HAProxy represents that type of utility for different OS. Free—based and open—source code makes this market offer quite profitable and safe. Do you need to rewrite the program for your situation? That is not a problem. It has a lot of different possibilities and options that support various algorithms for load balancing, monitoring, sniffing incoming traffic and primary function proxying TCP, UDP connections.
Setup this useful feature is quite simple!
Setup preparation and action
For correct operation, it is necessary to check the system requirements:
- Operating System: HAProxy can run on several operating systems, including Linux, FreeBSD and Windows;
- Memory: The memory requirement depends on the number of concurrent connections and the size of the configuration file. As a rule of thumb, you should allocate at least 2 MB per 1,000 connections;
- CPU: In general, a multicore CPU is recommended for better performance;
- Disk Space: The disk space requirement is minimal. However, you may need to allocate space for logs or other custom configurations.
If your system parameters are alright, we can start the installation with the commands below:
sudo yum update -yUpdate the index of packages with sufficient action, that helps install the actual version software.
sudo yum install epel-releaseThat command set up extended packages for your machine. They are not in the repository.
sudo yum install haproxyOutput in a CLI should look like in this picture:
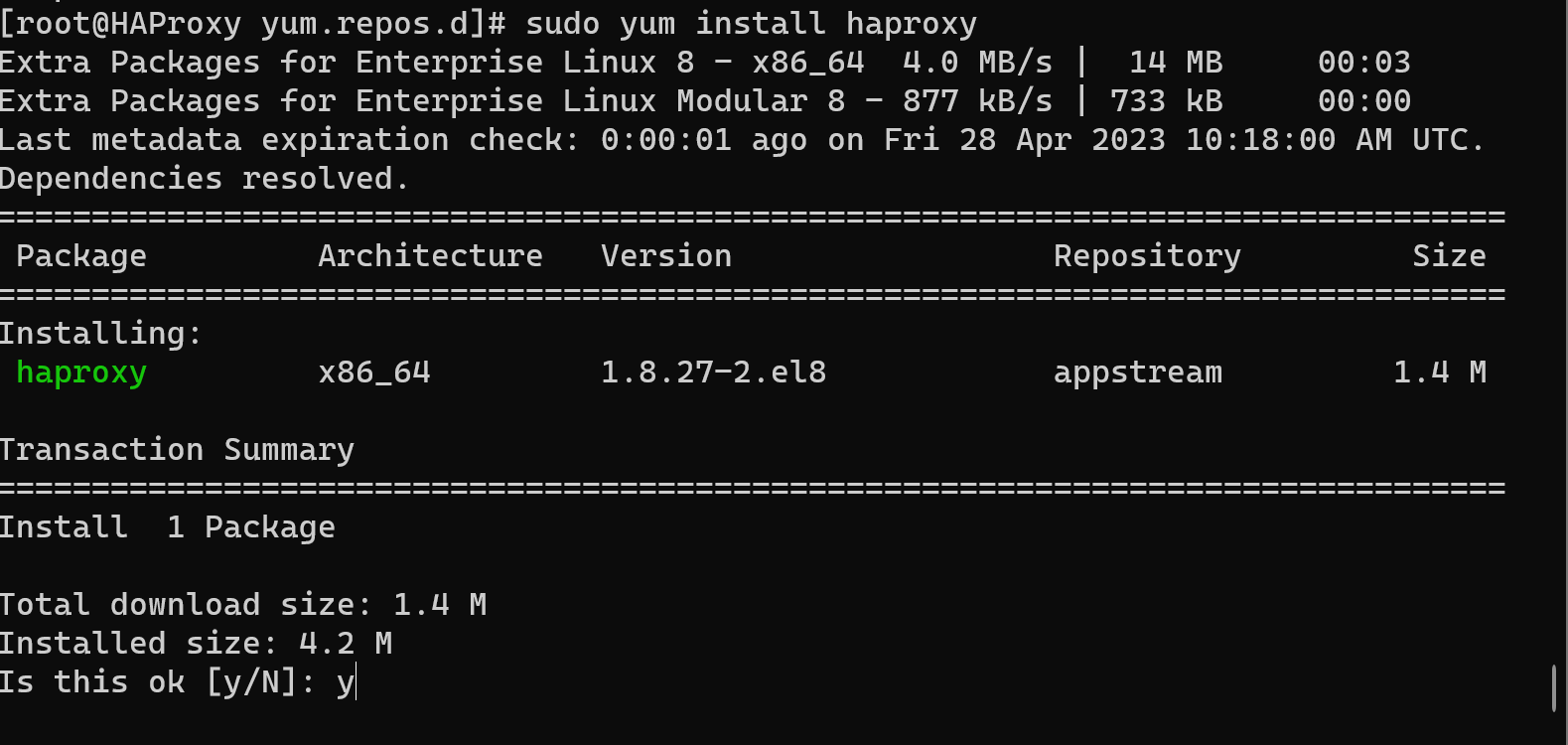
That is it! There is very little left: the configuration of your software.
Make a config
The process of writing configuration is quite creative. You need to calculate and think about the target of using this utility. I consider two situations of exploitation HAProxy, which could be a great number.
First and most popular usage HAProxy for proxying your data via server. Find the configuration file:
nano /etc/haproxy/haproxy.cfgThen open with anything text editor: nano, vim, etc. You can see three main blocks of configuration: global, defaults and a couple of sections, which need to build logic configuration. In my example, the config should proxying http connection via block “listen”. In the beginning, you need setup block “defaults”. The example shown in this picture:
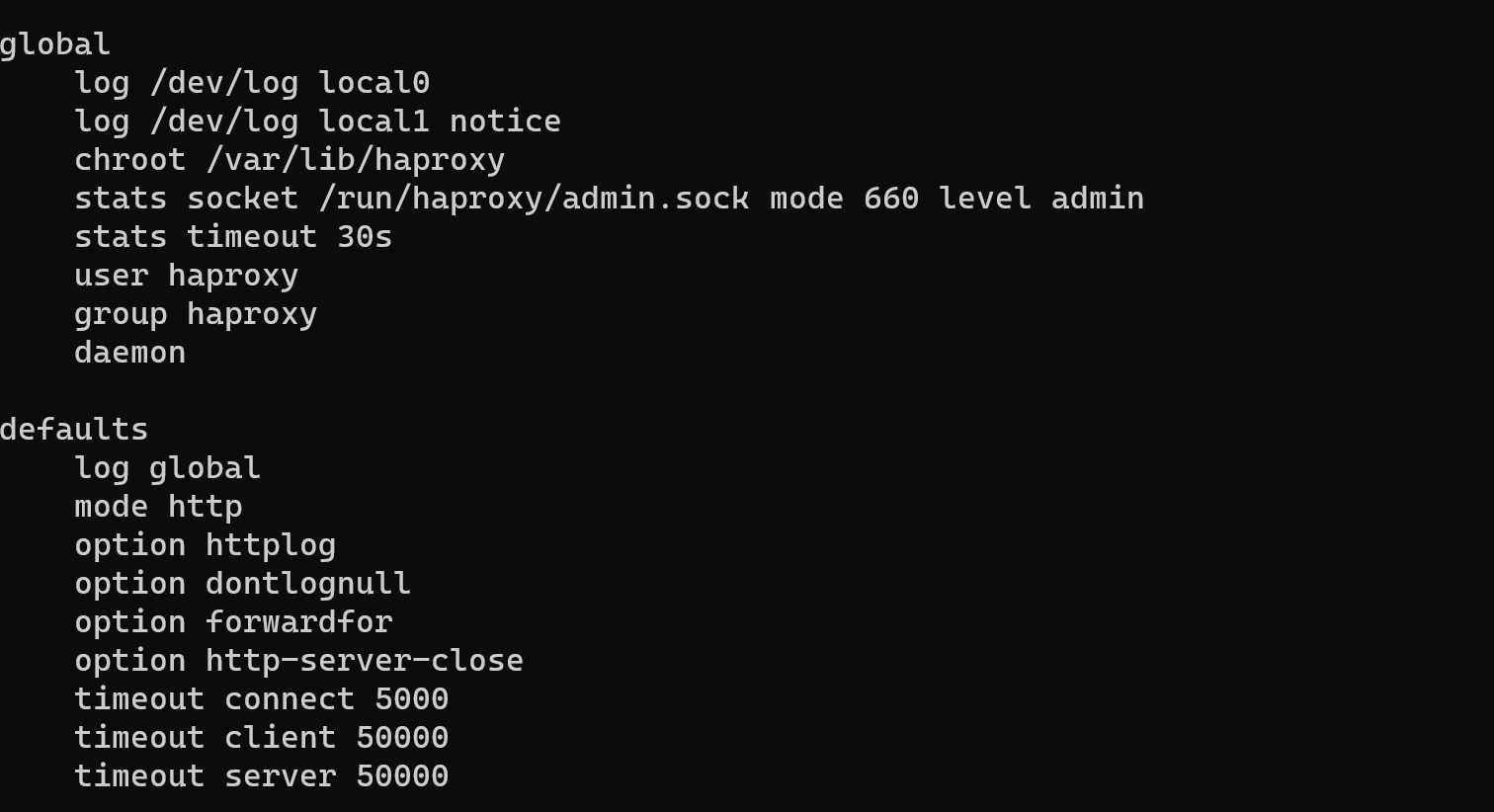
Let's describe these parameters:
- log global: Enables logging globally for all traffic processed by HAProxy;
- mode http: Specifies that HAProxy is operating in HTTP mode, which means it will be able to inspect and manipulate HTTP traffic;
- option httplog: Enables detailed HTTP logging, which includes request and response headers, along with other information such as client IP address and SSL version;
- option dontlognull: Prevents HAProxy from logging connections that don't receive any data.
If you use a UDP connection, then replace “TCP”. Let’s see the next block “listen”:
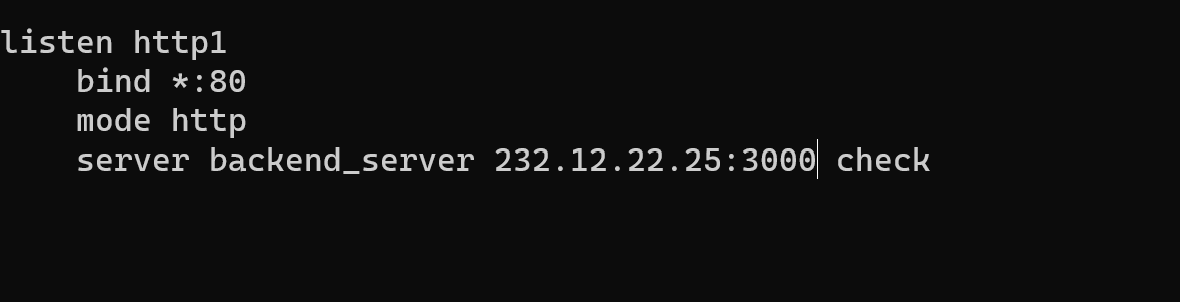
In the first line, we gave a name to our rule “http1” and then the parameter “bind” determine the source IP and port. I choose the symbol ”*”, because of having an indefinite machine for input. Write mode “http” and indicated the recipient server. The first — word means parameter, the second is the name of it, then indicates IP:port and the optional parameter “check”, which controls the availability connection.
Second use HAProxy for load—balancing your data via a proxy server. There are many methods and algorithms for redistribution load on a server:
- Round—Robin: methods allowed redistribution of incoming traffic equally on all servers, using a mathematical cycle, it is a practically proven and effective way to save the availability of your servers;
- Least Connections: methods route incoming traffic to the lowest—load server, which can be useful by using a keep—alive protocol connection;
- Source IP Hash: methods meaning calculating the hash value of all clients and comparing with the next connections, routing traffic on the same server.
Example of configuration displayed in the picture below:
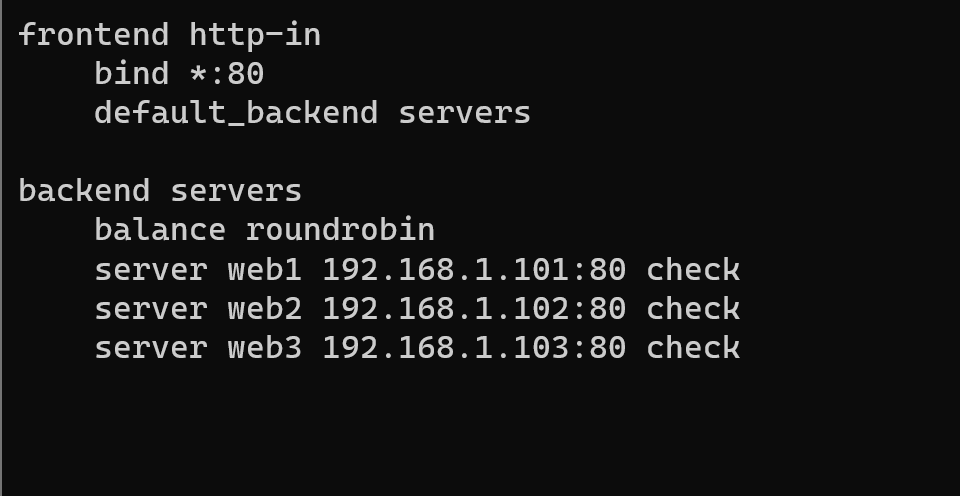
The parameters have been preserved the same, but the sections were a little bit modified. I add “frontend” and “backend” blocks. First means source traffic settings, and second target settings connection for the server. In “frontend” indicate IP:port and block’s target server. In “backend”, only the server address.
Then you need to compile your configuration and reload the service with the commands below:
haproxy -c -f /etc/haproxy/haproxy.cfgThe result of this command will be a message about the status of your configuration file and if was a mistake in your parameters, that will show “ALERT” and critical issue “WARNING”.
sudo service haproxy restartReload the service and test your connection!
Conclusion
HAProxy is a robust and versatile software solution commonly used for server load balancing, IP address masking to enhance basic anonymity, and flexible traffic proxying across diverse network scenarios.



