Linux plays a crucial role in modern network infrastructure, providing fine-grained control over system resources. One of the key aspects of this control is the ability to restrict user permissions. By default, Linux operates as a multi-user system, allowing multiple users to log in simultaneously and perform various tasks.
However, not all users require access to the full range of system resources or the same level of trust. To mitigate security risks and enforce the principle of least privilege, administrators employ a variety of techniques to limit user permissions, ensuring that each user has only the access necessary to perform their specific duties.
In this guide, we will explore one of the tools and methods commonly used to implement such restrictions effectively.
Software
Restricting user rights involves configuring security parameters of different config files: users, groups of users or processes. This can be done using built—in system permission, user groups or tools like AppArmor. System permission gives access to specific information systems subjects.
Availabilities such as writing, reading and executing access to the object of the file system. AppArmor and other software can be security modules which provide security services via the MAC concept and confinement process subset of the system.
Install and exploit
Before using the main utility update and upgrade your system :
sudo apt update —y && sudo apt upgrade —y
Install the needed package for creating a profile and log file:
sudo apt install apparmor—utils apparmor
And check utilities for the packet:
The process will be structured as follows: we create a profile for users that start scanning their actions and movement, start needed for the user program, which impact with their process and therefore we can collect all log files and set permission on it. First, create a profile with the user which you need to restrict:
sudo aa—genprof —h 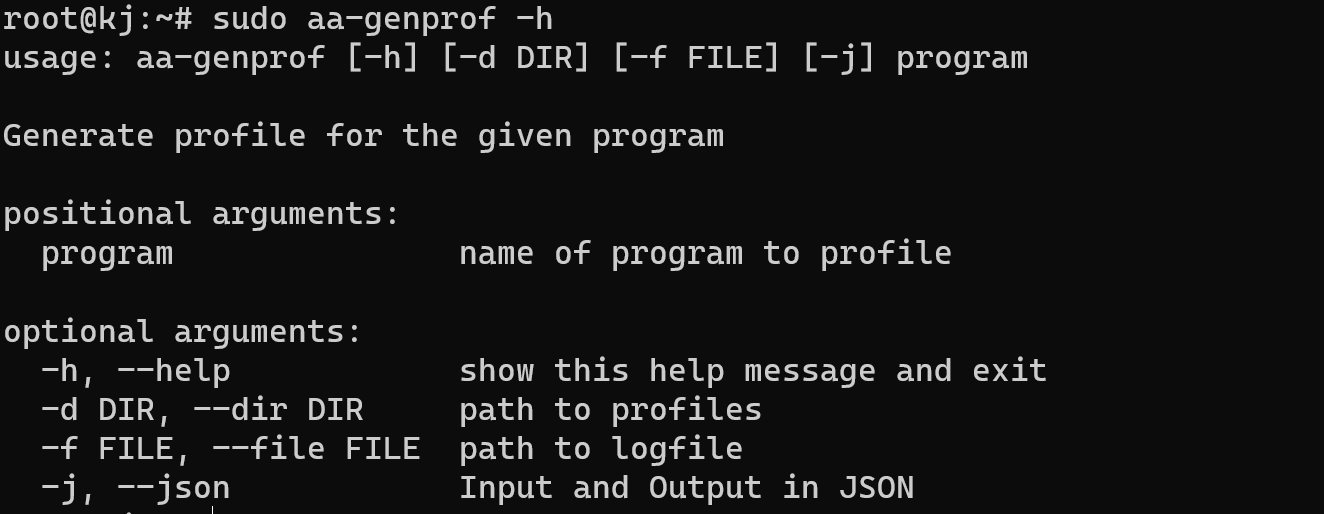
We can see a template of the program syntaxis and fill the gaps following that example:
sudo aa—genprof sudo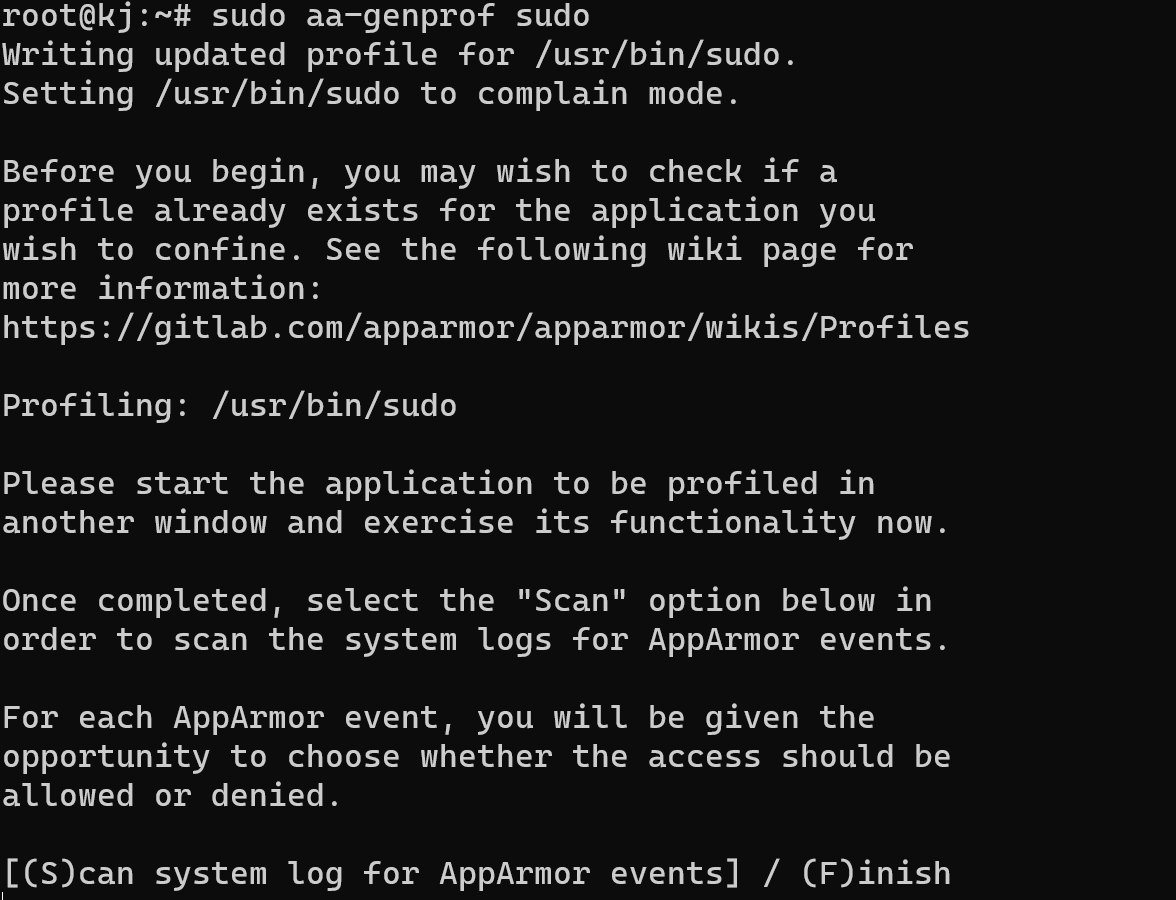
You can use any parameter on the screen below, but we use the default setting. Now, as you can see in the instruction, we have to create a new window in our remote program application:
Start all the programs, that you need to use and wait, now absolutely starting, requiring process writing in log journal:
Go to the previous window and stop the process with press the letter F on your keyboard:
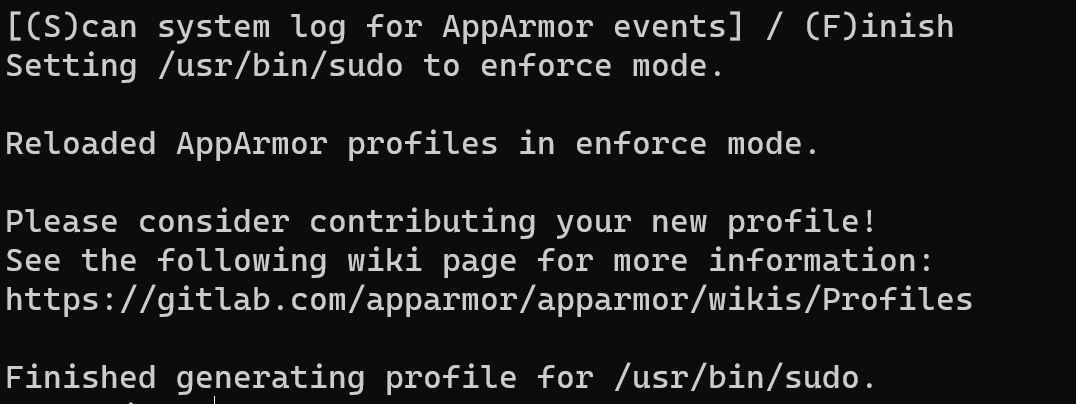
Go to the log files and check Apparmor kernel process starts right:
sudo journalctl —k
After we make sure that all processes start correctly, we need to update the log file in Apparmour :
aa—logprof
Start profile with enforce mode, which can turn up a system of MAC restrictions :
aa—enforce /usr/bin/sudo
Conclusion
Restricting user permissions is a critical component of effective Linux system management. It enables administrators to grant users access only to the resources they need, significantly reducing the risk of unauthorized actions and potential security breaches. One powerful tool for achieving this is AppArmor, which allows defining detailed security profiles for users and their processes.
By following the steps in this article, administrators will learn how to create and manage AppArmor profiles, analyze related log files, and enforce strict permission controls. Implementing these measures contributes to a more secure and stable Linux environment.
Stay tuned for the next article, where we will explore more advanced and flexible AppArmor configurations to further enhance your system’s security.



