Introduction
In this publication I will demonstrate how to identify vulnerabilities in your system. Server security must be a priority! After all, every device can be hacked, so software developers close open holes in their programs as soon as possible, thus we need to update the "software" regularly, otherwise an attacker will take advantage of the vulnerability and cause damage to the server, and maybe even to the whole company.
Facebook was hacked for 3 years from 2019 to 2021, causing more than 950 million users to be published. Among this data was users' phone numbers, mailing addresses, dates of birth, and other personal information. All this can be avoided if you take the time to be cyber secure, and to keep an eye on the software you use.
How does the cyber attack work?
Kill-chain is a sequence of actions which an attacker carries out to gain access to a server.
There are in total 4 stages of a kill-chain:
- Gathering information about the system (what services are running; what software version).
- Search for vulnerabilities in the system.
- Creation or use of malicious code (exploit).
- Delivery exploit to the victim (by sending an email, an infected site or in some other way).
Warned is armed, because knowing the kill-chain, it is possible to secure the server as much as possible, thereby making it difficult for an attacker to access the server.
How to check the system?
The nmap utility is used to check the system, install it following the instructions.
apt install nmap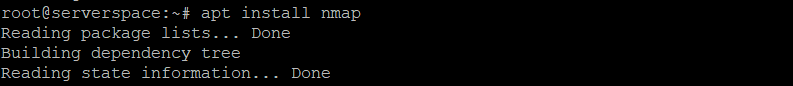
Let's check what services are running on our server.
nmap 127.0.0.1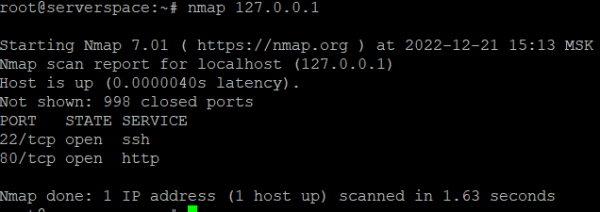
As we can see, on my test server I have the "ssh" service running on port 22 and the "http" service running on port 80.
To check for open "udp" ports, use the command below.
sudo nmap -sU 127.0.0.1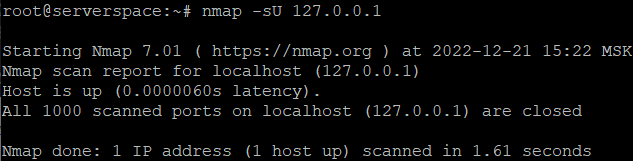
There are no open "udp" ports on the test server.
Through the eyes of an intruder, he obtained information about 2 open ports (22;80) and also the server is running the "openssh" service, through which he can launch a cyber attack, if this software has vulnerabilities.
To find out what version the software is installed, use the command.
nmap -sV 127.0.0.1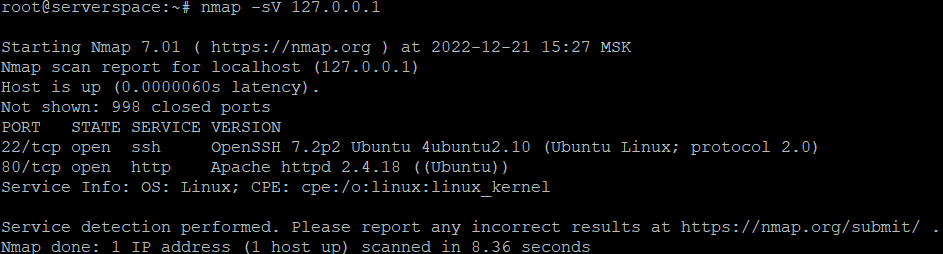
We have discovered that an old version of the "OpenSSH" utility is installed on the server, so let's check it for vulnerabilities.
To find vulnerabilities in the tools refer to the database of Google;Cisco;CVE, where versions of different software, and their vulnerabilities were found by other people.
Looking at the history of the updates of "OpenSsh", namely version 7.2.p.2, we find out about an open vulnerability in the running software.
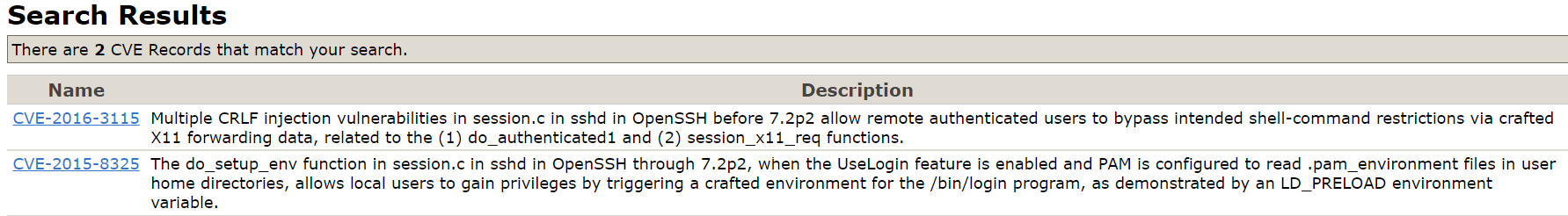
Only two vulnerabilities, but they give full access to superuser rights, the attacker has only to place the exploit on the victim's server by delivery, it can be: phishing, infected email or website.
Conclusion
In this publication I analyzed a test server for vulnerabilities that could be very damaging to a company.
By the example of Facebook, which has exposed over 950 million users - you should install it on your operating system as soon as an update is released and you should update your software. Increase network security by adding intermediary devices, and adding different degrees of security to your LAN.




