The main reason for changing a user password is to prevent unauthorised access by cybercriminals. Cybercriminals often try to crack your login key through brute force attacks or by leaking data from other systems, which can give them the opportunity to guess your password correctly.
So changing your passwords frequently can help protect your personal or your organisation's information. But what if you forget the credentials for your Linux server? And alternative authentication protocols such as TACACS+ or RADIUS are not configured. In this tutorial we will look at the way to change them.
Warning. This article presents information about the security mechanism for educational purposes only and does not call for anything!
Bypass Method
This approach is often used because of the peculiarities or vulnerabilities of the various ways of running the kernel through the GRUB boot loader, but first we need to explain how the authentication system works!
The machine stores credentials in hash form with salt, that is, random sequences of values that pass off as a more complex and secure password between different attacks. When a user tries to connect, Linux compares the hash of the password entered with the stored credentials, if they match then the user can gain access, otherwise entry is denied, which is controlled by a kernel module. Also in a modern system there is PAM which combines different authentication methods and has its own peculiarities. We will focus on the basic access verification model.
To bypass the system requirements we need to disable or replace the kernel module, but how to do it? Let's go back to the text above with the GRUB boot loader. At startup time, we can select the boot type as in the screen below:
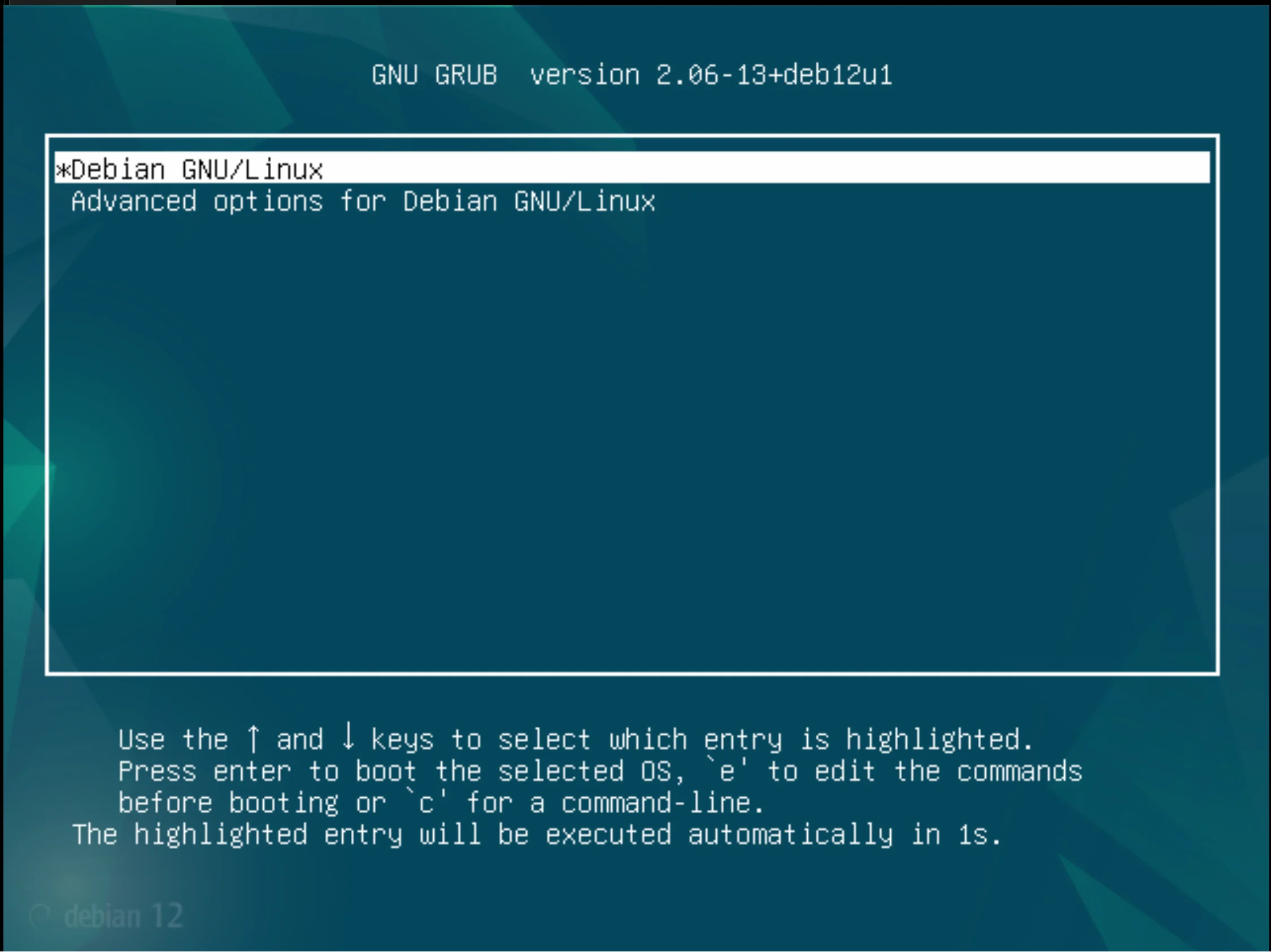
Click the E button to edit the startup configuration, right where we specify the startup method. Scroll down and add this line to the line that starts with the word linux:
init=/bin/bash If the drive is encrypted, add this:
plymouth.enable = 0 Also if this line has ro in it, change them to rw:
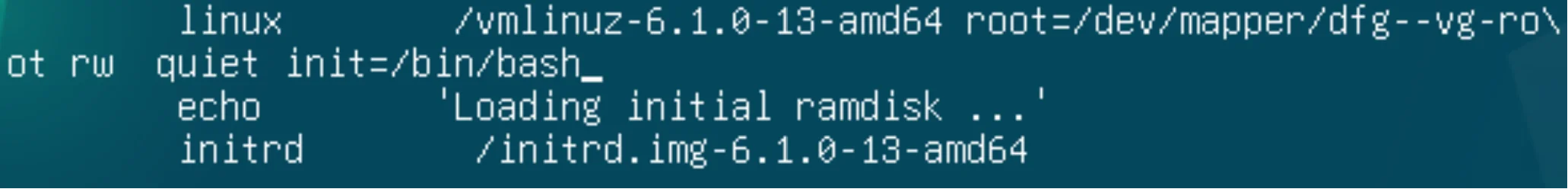
Great!!! Press Ctrl + X or F10 to save the changes and wait for the system to boot, after checking you will see a terminal window with bash. To change the password, use the command below:
passwd root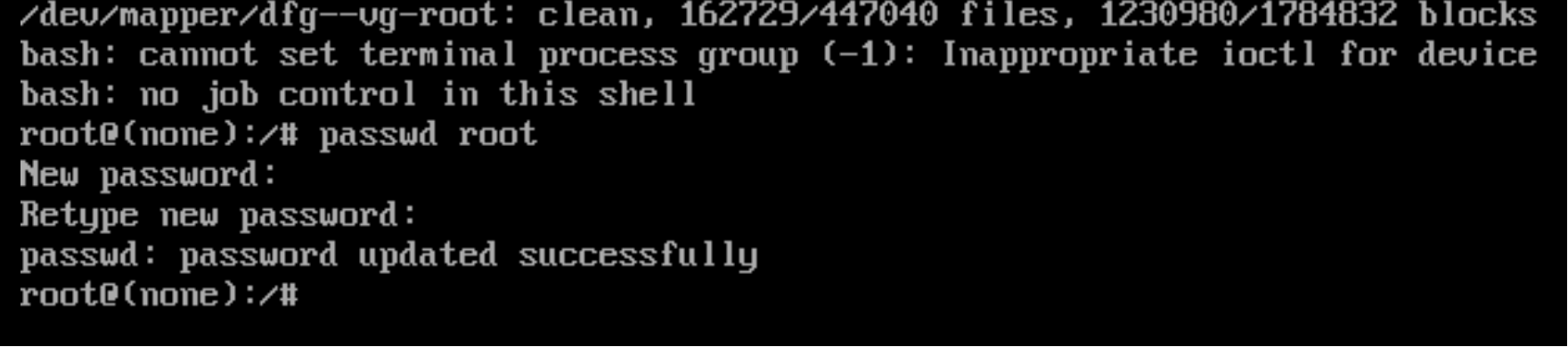
Reboot the system and the changes we made to the config will reset. But the password you set will remain!
In conclusion, the need to change user passwords is due to the constant threat of unauthorised access from intruders in the digital space. Changing passwords frequently is a proactive measure to reduce the risk of cybercriminals exploiting vulnerabilities, be it brute-force attacks or compromising data through external hacking. This practice is critical to protecting personal information and organisational security.
Conclusion
Resetting your Linux password is an essential security measure to protect your system from unauthorized access. Whether you’ve forgotten your credentials or need to update them to maintain strong security, knowing how to reset a password ensures continued access and system integrity. By following the steps outlined in this tutorial, you can regain control of your account safely and efficiently, reinforcing the overall security of your Linux environment.
FAQ
- Q1: Can I reset my Linux password without physical access to the machine?
A1: No, you generally need either physical access or administrative privileges through another account to reset the password using the methods described. Remote password resets typically require preconfigured remote management tools. - Q2: Will this method work on encrypted drives?
A2: If your drive is encrypted, you may need to add additional parameters (like plymouth.enable=0) to bypass the encryption prompt during boot. Otherwise, you will not be able to access the system to reset the password. - Q3: Does resetting the password affect my files or system settings?
A3: No, changing the password only updates the authentication credentials. Your files, applications, and system settings remain unchanged. - Q4: Can this method be used on all Linux distributions?
A4: Yes, this method using GRUB and init=/bin/bash works on most Linux distributions that use GRUB as the boot loader, including Ubuntu, Debian, CentOS, and Fedora. - Q5: Is it safe to reset the root password using this method?
A5: Yes, if done carefully and responsibly. However, it should only be performed by authorized users. Unauthorized use can be considered a security breach. - Q6: How often should I change my Linux passwords?
A6: It’s recommended to change passwords periodically, especially for root or administrative accounts, and whenever there is a suspicion that credentials may have been compromised.



