Debian superuser rights (sudo, visudo)
General information
Linux operating systems implement the principle of differentiating user privileges, meaning that different accounts have different amounts of access rights to directories, files, and programs. The maximum rights are granted to the built-in root account. Newly created user accounts are usually significantly restricted in accessing system configuration files, managing services, and installing and deleting software packages. However, working in the operating system under the root account is strongly not recommended, primarily for security reasons. In this case, the sudo command line utility comes to the rescue.
The sudo command allows running individual commands with increased privileges (by default, with root rights) using an unprivileged account. Let's see what is required for this utility to work.
Installation and configuration
In Ubuntu OS, sudo is enabled by default, and in Debian, if the corresponding package was not selected during the installation process, the following picture will most likely be:
root@debian10:~# sudo
-bash: sudo: command not foundSo, you need to install the missing package. Update repository information and install sudo:
apt-get update
apt-get install sudoWe are waiting for the end of the process:
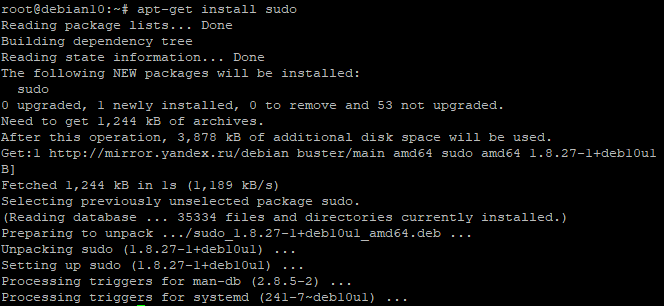
After a successful installation, you will need to configure sudo to determine which users or groups will be able to use privilege escalation and to what extent. All these settings are stored in the configuration file /etc/sudoers, however, it is strongly discouraged to directly make changes to it. For these purposes, a special command is used:
visudowhich launches a text editor with a configuration file:
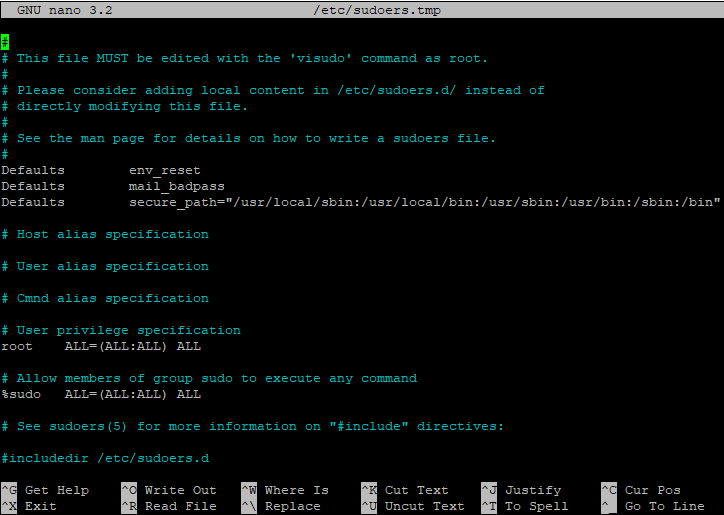
Two lines are responsible for granting rights:
root ALL=(ALL:ALL) ALL
%sudo ALL=(ALL:ALL) ALLThe first line sets the rights for the root account, the second sets the rights for members of the sudo group that was created when the package was installed (the % sign in front of the name means that the name belongs to a user group).
Accordingly, we have two main ways to grant the user account the right to use sudo:
Add a user account (e.g. user) to the sudo group on the server:
usermod –a –G sudo userAfter changing the group membership, you will need to re-log into this account to apply the new configuration. This method is recommended in cases where the user must be granted full rights.
Create a new entry in the file, for example, for the user account. We add a line similar to root:
user ALL=(ALL:ALL) ALLAdding a new entry is recommended in cases where the list of privileges will be adjusted (more on that later). If we made changes to the file, we need to save them by pressing the keyboard shortcut Ctrl-O and exit the editor - Ctrl-X.
Now you can check the correct operation:
user@debian10:~$ sudo cat /etc/sudoers
[sudo] password for user:The sudo command asks for the password of the current user (in this case, user) - enter it, and if everything is done correctly, we will see the contents of the system configuration file.
Fine-tuning
Thus, an ordinary user can run commands with the rights of the root account without knowing her password. This is very convenient, but it can be unsafe - is it possible to limit the range of commands that can be executed using sudo? Yes, and the same configuration file will help us with this. We start visudo again and we understand further. We are interested in the parameters specified after the username:
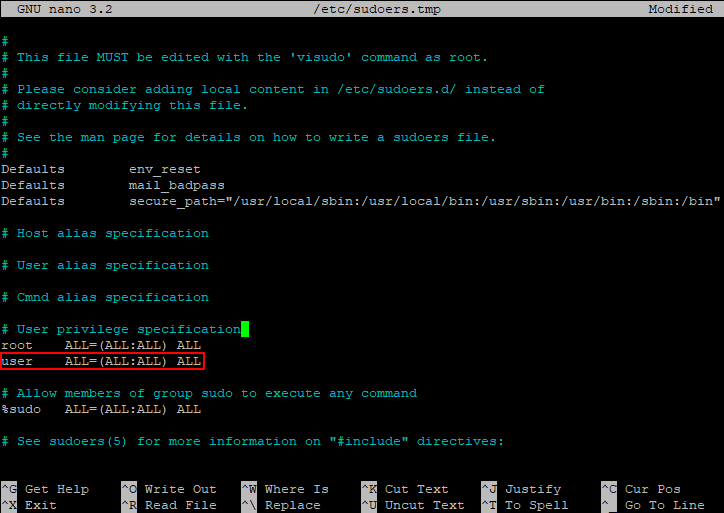
We will analyze them in more detail:
- ALL= (ALL: ALL) ALL - the first parameter determines which host the configuration is applied to. When using a dedicated server, the parameter can be left unchanged;
- ALL=(ALL: ALL)ALL - the parameters in brackets determine the authority of which user (first parameter) and/ or group (second parameter) the command will be executed. By default, sudo executes the command as root, but when starting with the –u switch, you can specify a different account, and with the –g switch you can specify another group whose privileges will be used at startup;
- ALL=(ALL: ALL)ALL- the third parameter determines which files and commands these settings belong to.
Based on the foregoing, if necessary, determine the list of allowed commands, replace the last parameter ALL with what we need, listing the commands separated by commas. For example, the line:
user ALL=(ALL:ALL) /sbin/shutdown –r, /bin/catgives the user the right to use sudo to reboot the server with sudo /sbin/shutdown –r and view files using sudo /bin/cat. Other commands through sudo will not be executed. For example, when you try to shut down the server with the command sudo /sbin/shutdown –h, we get the answer:
Sorry, user user is not allowed to execute '/sbin/shutdown -h' as root on debian10.Useful
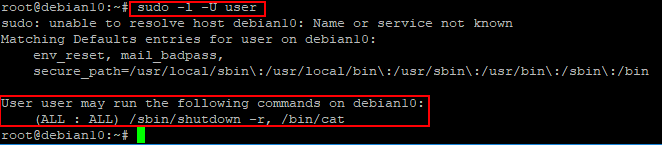
You can see the list of privileges by running sudo –l (the list for the current user will be displayed), or sudo –l –U user (the list of user privileges will be displayed):
The composition of sudo includes the sudoedit command, which launches a text editor with the specified file immediately with elevated privileges, that is, instead of the command:
sudo nano /etc/network/interfacescan run:
sudoedit /etc/network/interfacesIf you need to work in elevated privilege mode for a long time and it is inconvenient to enter sudo for each command, you can run an instance of the command interpreter through sudo:
sudo bashand continue to work in it - all teams will be launched with elevated rights. Upon completion, exit the interpreter with the exit command.
 700
300
700
300
 700
300
700
300
 700
300
700
300


